Windows Shell Items Analysis
Deep dive of what we can do with Shell Items on windows

The registry is a hierarchical database, The Windows Registry holds configuration information about all the applications on the system, user-specific settings, configuration of various hardware devices used by the system, settings for all the software on the system, etc.
DIVE INTO THE REGISTRY, ONE OF THE FIRST THING WE NEED TO KNOW IS… WHERE IS IT? AND WHERE IS THE KEY COMPONANT? HOW IS IT ORGANIZED? Why is this registry path useful?
Let’s assume you downloaded a video attachment from an email. When you opened that video, you noticed that it also opens up the Notepad application on its own and it has some content written in a foreign language. You closed that video, but every time you restart your system, you notice that the Notepad application opens automatically and the same foreign language content is displayed.
What is happening here is:
when you downloaded the video attachment, you accidentally downloaded some malware onto your computer. The video could have been from a malicious source. That malware has modified the autostart location in the registry to bring up the binary for Notepad whenever the system is rebooted. and WE DIVE INTO THAT IN THE PRACTISE SECTION!
The registry is structured very similarly to the Windows directory/subdirectory structure. You have the five root keys or hives and then subkeys. In some cases, you have sub-subkeys. These subkeys then have descriptions and values that are displayed in the contents pane. the values are simply 0 or 1, meaning on or off, but also can contain more complex information usually displayed in hexadecimal.
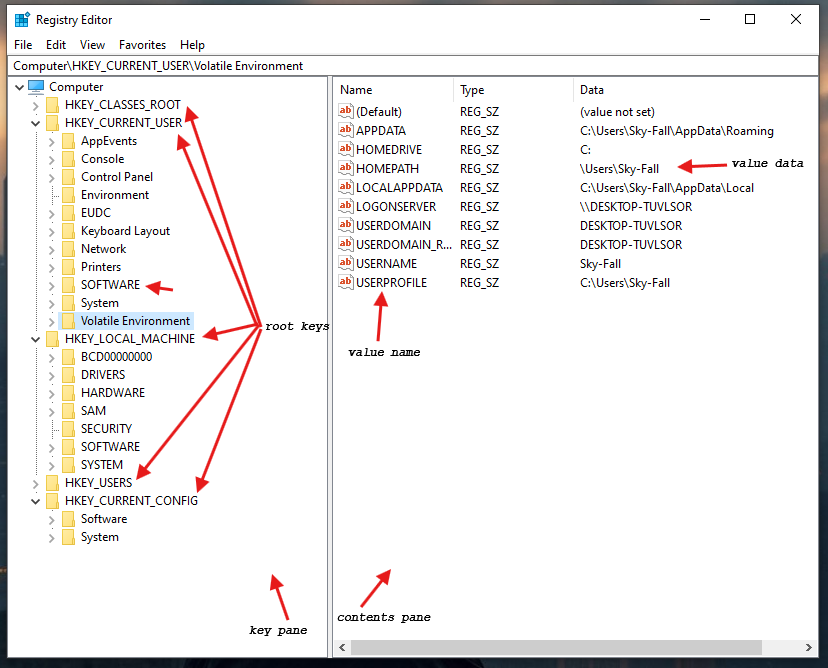
Inside the registry, there are root folders. These root folders are referred to as hives. There are five (5) registry hives.
HKEY_USERS: contains all the loaded user profiles
HKEY_CURRENT_USER: profile of the currently logged-on user
HKEY_CLASSES_ROOT: configuration information on the application used to open files
HKEY_CURRENT_CONFIG: hardware profile of the system at startup
HKEY_LOCAL_MACHINE: configuration information including hardware and software settings
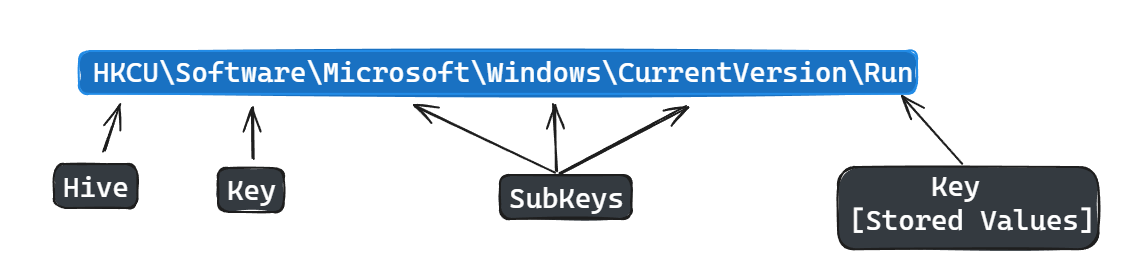
Keys:
Similar to folders(keys) and subfolders(subkeys),
produces a folder directory hierarchy
Values:
Data stored within a key, contains data in the form of strings, binary data, integers, and lists.
where the most valuable forensics data is found
Collection of data files called hives.
When viewed in a registry viewer, hive names are used:
Hkey_local_machine(HKLM) contain hives:
SAM
Security
system
software
hkey_current_user(Hkcu) contain hive:
Investigating the Windows registry is quite a difficult task because to investigate it properly, the registry needs to be extracted from the computer. Extraction of the registry file is not just a normal copy-and-paste function.
Since registry files store all the configuration information of the computer, it automatically updates every second. To extract Windows registry files from the computer, investigators have to use third-party software such as FTK Imager.
FTK Imager is one of the most widely used tools for this task. Apart from using third-party software, some research has been carried out to demonstrate how to extract registry information from Windows CE memory images and volatile memory (RAM). The steps to extract registry files from Access Data FTK Imager are as follows:
Step 1: Open access data ftk imager and click on the “add evidence item” button then select the “logical drive” radio button
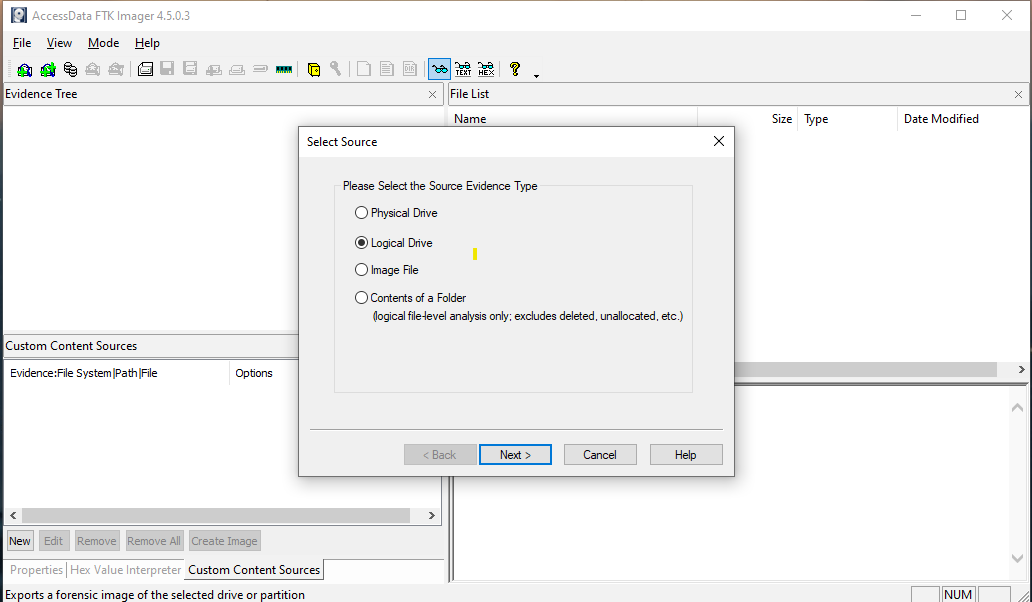
note:
Physical Drive: Extract from a hard drive
Logical Drive: Extract from a partition
Image File: Extract from an image file
Contents of a Folder: Logical file-level analysis only: excludes deleted files and unallocated space
Step 2: Then select the source drive and after that scan “MFT” by expanding “evidence tree”, go to windows/system32/config/
Step 3: Export the registry file by clicking the “export files” button then select the destination folder
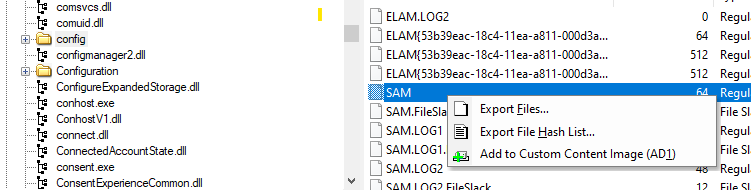
We are going to open it in the registry explorer to view the content we have exported
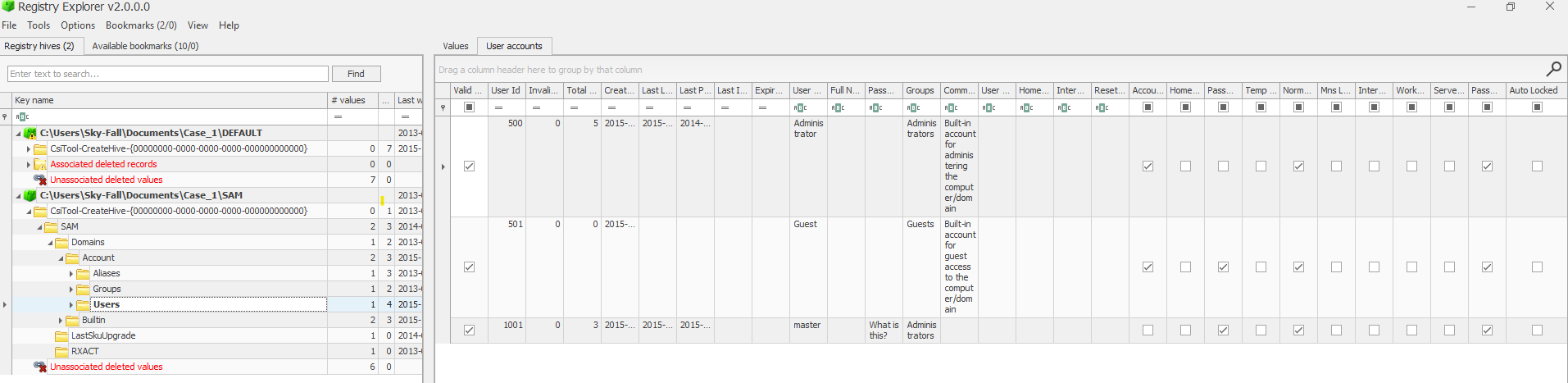
Registry hives have unallocated space similar to filesystems
A deleted hive key is marked as unallocated
recovery of unallocated keys possible
keys
values
timestamps
lack of anti-forensics tools to completely wipe unallocated registry hive data recovery of deleted keys possible
Windows Version and Owner Info
Computer Name
Time Zone Setting
The system’s time zone is stored in System\ControlSet001\Control\TimeZoneInformation. Access Time Tracking
By default, the last access time tracking is turned off (NtfsDisableLastAccessUpdate=1). To enable it, use: fsutil behavior set disablelastaccess 0 Windows Versions and Service Packs
The Windows version indicates the edition (e.g., Home, Pro) and its release (e.g., Windows 10, Windows 11), while Service Packs are updates that include fixes and, sometimes, new features.
Enabling Last Access Time
Network Information Details
CLIENT-SIDE Caching (CSC)
AutoStart Programs
Shellbags
USB Information and Forensics
Volume Serial Number
Shutdown Details
Network Configuration
For detailed network interface info, refer to System\ControlSet001\Services\Tcpip\Parameters\Interfaces{GUID_INTERFACE}.
First and last network connection times, including VPN connections, are logged under various paths in Software\Microsoft\Windows NT\CurrentVersion\NetworkList.
Shared Folders
Shared folders and settings are under System\ControlSet001\Services\lanmanserver\Shares. -The CLIENT-SIDE Caching (CSC) settings dictate offline file availability. Programs that Start Automatically
Paths like NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Runand similar entries under Software\Microsoft\Windows\CurrentVersion detail programs set to run at startup. Searches and Typed Paths
Explorer searches and typed paths are tracked in the registry under NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer for WordwheelQuery and TypedPaths, respectively. Recent Documents and Office Files
Recent documents and Office files accessed are noted in NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs and specific Office version paths. Most Recently Used (MRU) Items
MRU lists, indicating recent file paths and commands, are stored in various ComDlg32 and Explorer subkeys under NTUSER.DAT.
User Activity Tracking
Shellbags Analysis
Shellbags, revealing folder access details, are stored in USRCLASS.DAT and NTUSER.DAT under Software\Microsoft\Windows\Shell.
Use Shellbag Explorer for analysis.
USB Device History
HKLM\SYSTEM\ControlSet001\Enum\USBSTORand HKLM\SYSTEM\ControlSet001\Enum\USB contain rich details on connected USB devices, including manufacturer, product name, and connection timestamps.
The user associated with a specific USB device can be pinpointed by searching NTUSER.DAT hives for the device’s {GUID}.
The last mounted device and its volume serial number can be traced through System\MountedDevicesand Software\Microsoft\Windows NT\CurrentVersion\EMDMgmt, respectively.
In this show, I will show you two tasks using the Windows registry.
first, I will configure an application to start whenever a user logs in to the computer
then I will show you how can find information about recently used documents, within the registry.
We will then discuss about the significance of these two tasks in digital forensics.
first, I will add an entry in the registry to start up the Notepad application whenever a user logs into the system. within the: Hkey_local_machine/Software/Microsoft/windows/current version/Run I will add a new string value to this key, just by performing a right click in this white space, the name is provided as notepad
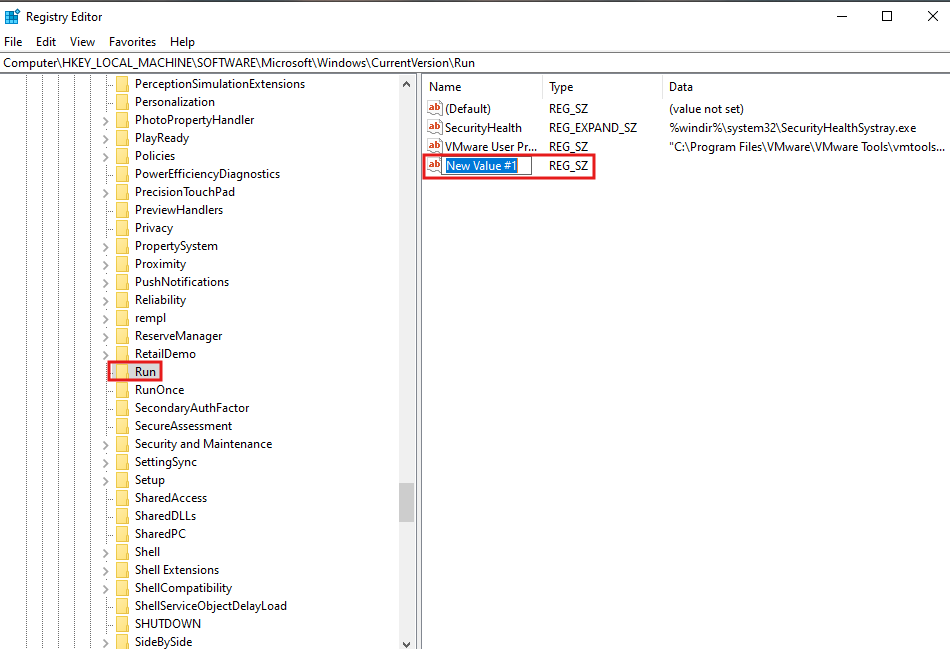
when I double-click this name, I can add the value, and the value is the absolute path of the Notepad executable.
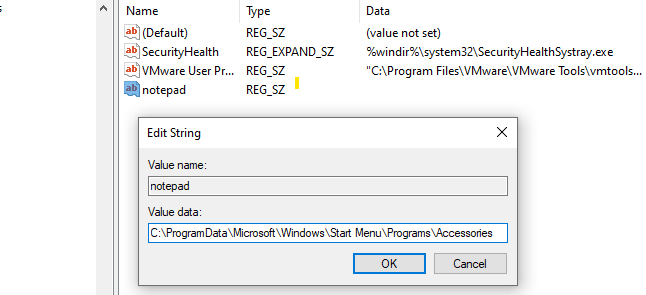
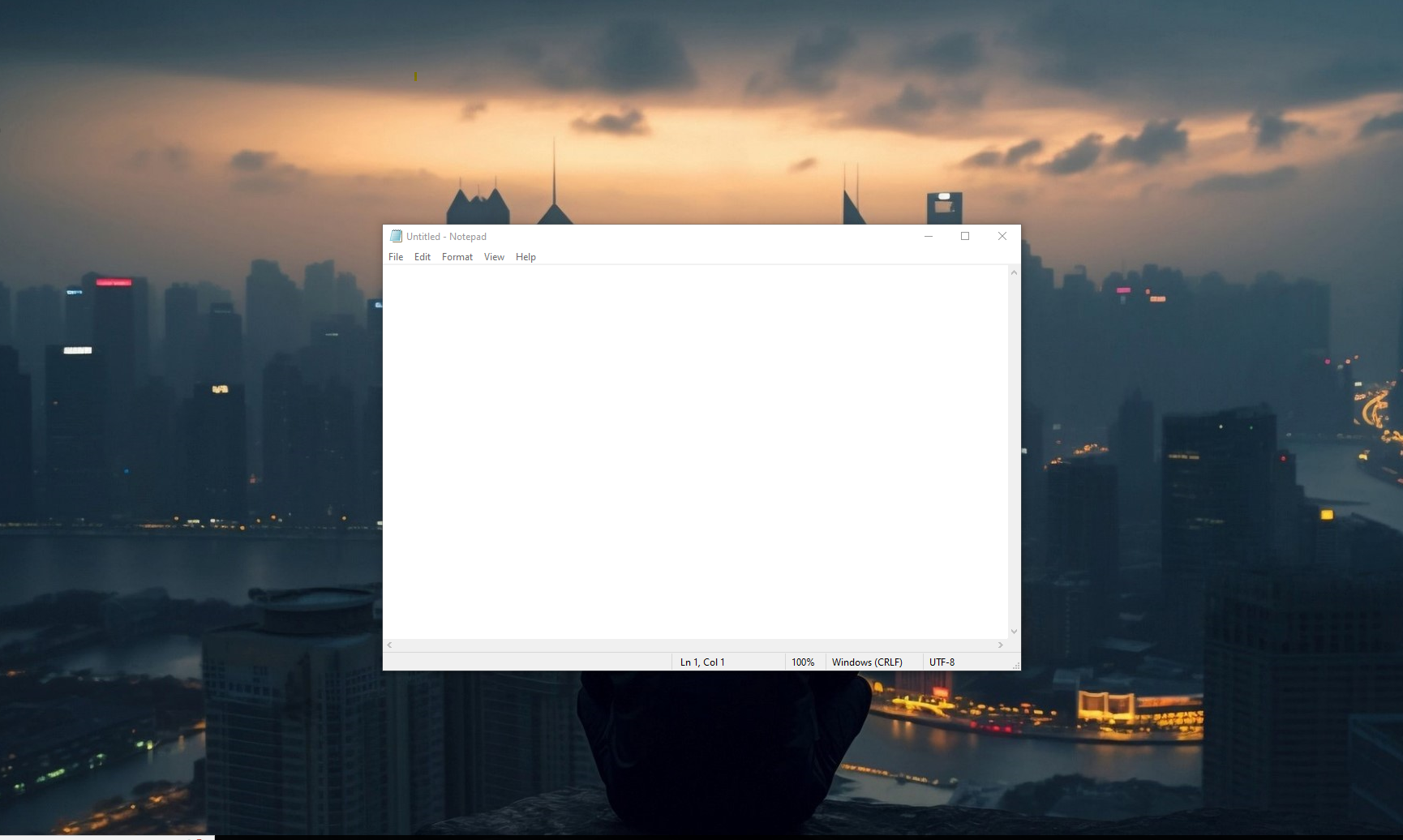
now I log out and back again to see what happened… and here we go :) you can see that right after a user logs in to the system notepad application is started automatically. now this is a legitimate application, cyber attackers may modify the registry run key, and configure malicious applications to run, when a user logs in. knowing where the registry Run key is, may help you identify some malicious autostart programs on the computer
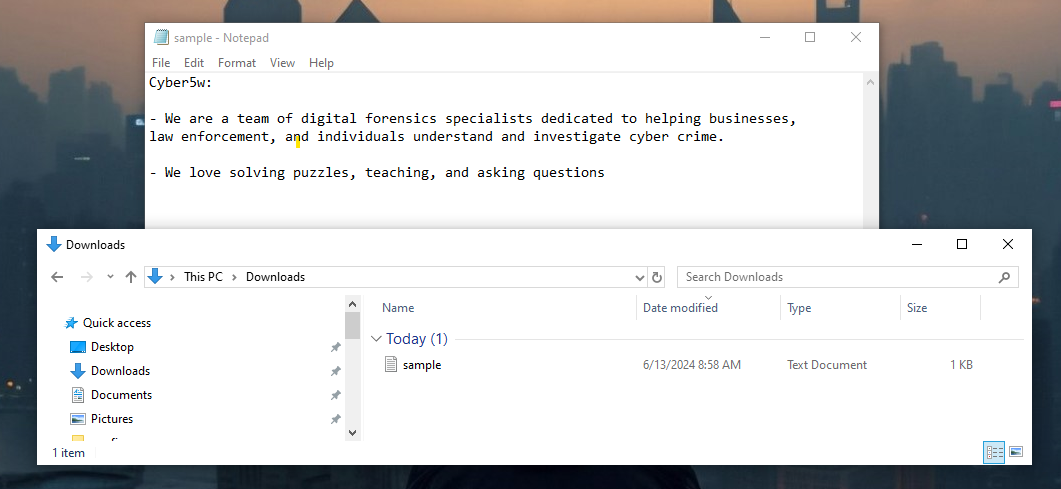
Let’s take a look at another one: I will edit this text file “sample”, add some text, and save this file.
with the registry, I will show you that we can find information about recently modified files. I will open the registry editor application again, within the HKEY_current_user/software/Microsoft/windowos/current version/explorer/recentdocs key. within the text subkey, we will find information about recently modified text files on the system. here in the center pane, we can find one entry the name zero
the data appears to be hex bytes. and I will double-click the name
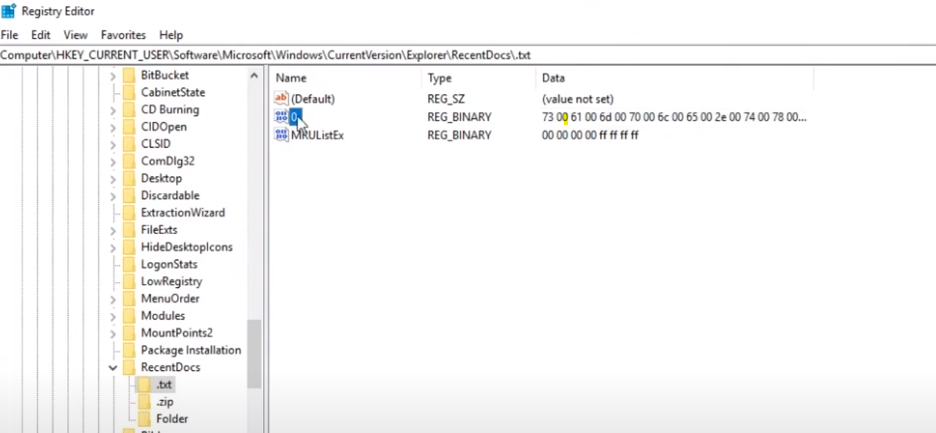
In this window, you can see the same hex data in the center. the hex data is displayed in ASCII in the right pane, here you can see the same of name the text file I modified recently, the sample
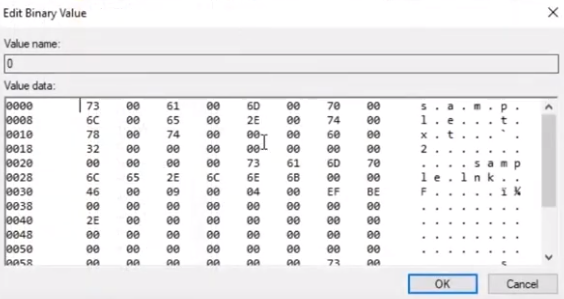
using tools to parse the registry, you can find the timestamp of when a file was recently modified. There are many more FORENSICS ARTIFACTS WITHIN THE REGISTRY WHEN YOU ARE AWARE of THE ARTIFACTS YOU CAN FIND, AND WHERE YOU CAN FIND THEM, YOU CAN EASILY LOCATE THEM DURING AN INVESTIGATION. WITHIN MEMORY DUMPS, YOU CAN RECOVER REGISTRY ENTRIES THAT UNDERWENT MODIFICATION RECENTLY
This blog is authored by Asem Ashraf.