CyberGate Technical Analysis
Analysis of CyberGate RAT

As a malware analyst, your analysis environment is considered your friend, it can make your life easier and save you a lot of time if you just invest time on it once, and it also can make your life a hell if you just decided to ignore updating it and equip it with the tools that can cut the time for you.
In this blog post, we will talk about how to set up a Pro Malware analysis environment equipped with modern tools, scripts, and plugins.
Keep in mind that this topic is unlimited and can always be extended more and more, so if you have an interesting addition don’t hesitate to reach out to me here.
Note: we are not going to mention two tools that can do the same thing if there isn't a difference.Let’s split our discussion by the different stages we encounter during our analysis.
Let’s start simple with basic triaging tools
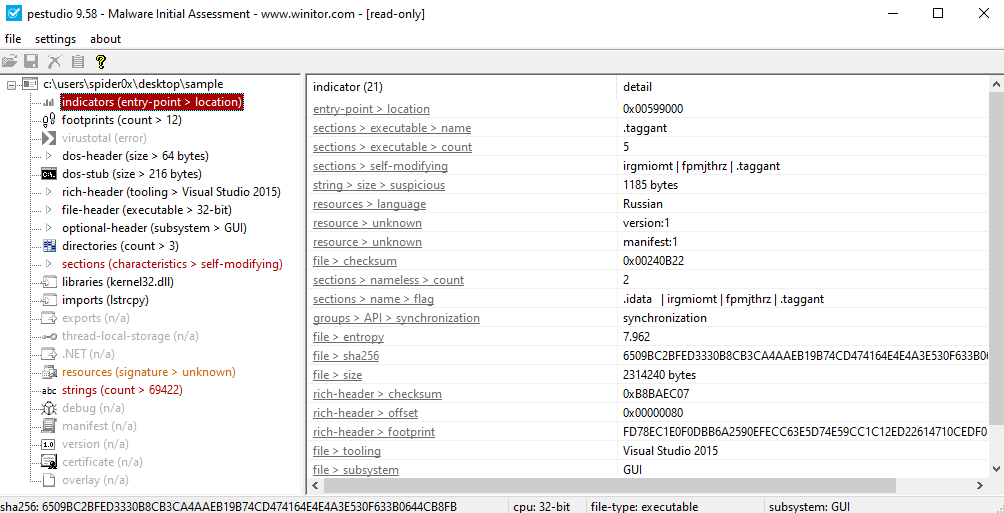
pestudio is a well-known tool used in initial assessment for any malware sample, as it has a lot of features scattered among multiple tools in one place, like libraries, Imports, Exports, Sections, Strings, Entropy, File Headers, and many others.
Also, the tool performs some checks on the sample and gives you some red flags it has observed that you can keep in mind for your analysis.
FLOSS is a strings parsing tool that is much smarter than other tools that just pull any ASCII characters followed by a null termination, this tool has additional capabilities that enable it to decode strings obfuscated inside the malware statically, things like Stack Strings, Encrypted Stack Strings, and some times it can do a great job on identifying string decryption functions and emulating its results.
here we can see the output strings from decoded strings inside a malware sample that can tell us that we are dealing with a stealer here easily without any analysis of the code.
Krypto ANALyzer is a nice plugin built into PEID tool that serves very well at identifying cryptographic algorithms that may be missed by other tools.
CryptoTester is a great tool that works similarly to Cyberchef, but it has a different interface and feels more simple to deal with encryption algorithms through it.
Sysmon is a Windows system service and device driver that monitors and logs system activity to the Windows event log, configuring your analysis workstation to use this additional log service can provide you with really good insights about what is happening in your system, It can log many different events you can find a long list of its logged events on the rule you are using, here is the most used rules repository, but generally here some important ones there,
What makes this tool great for us is that we can parse it easily using any scripting language like PowerShell.
here is an example of one linear PowerShell that managed to extract all the DNS requests made by the sample.
Get-WinEvent -FilterHashtable @{Logname = "Microsoft-Windows-Sysmon/Operational" ; ID = 22 ; StartTime = "7/31/2023 1:24:25"} | Where-Object {$_.properties[7].Value -match "orxds"} | Format-List @{label = "DNS Requested Domain" ; Expression = {$_.properties[4].value}},@{ label = "Image" ; Expression = {$_.properties[7].value}} 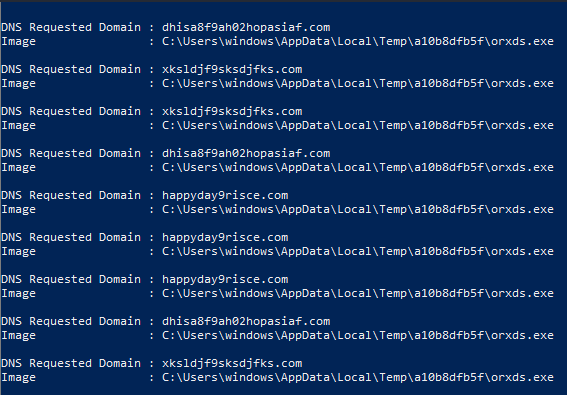
Here we can find all the child commands executed by the sample using one PowerShell linear.
Get-WinEvent -FilterHashtable @{Logname = "Microsoft-Windows-Sysmon/Operational" ; ID = 1 ; StartTime = "7/31/2023 1:24:25"} | Format-List @{label = "CommandLine" ; Expression = {$_.properties[10].value}}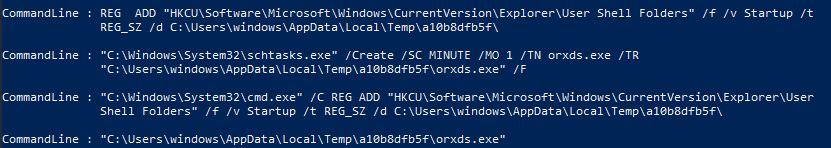
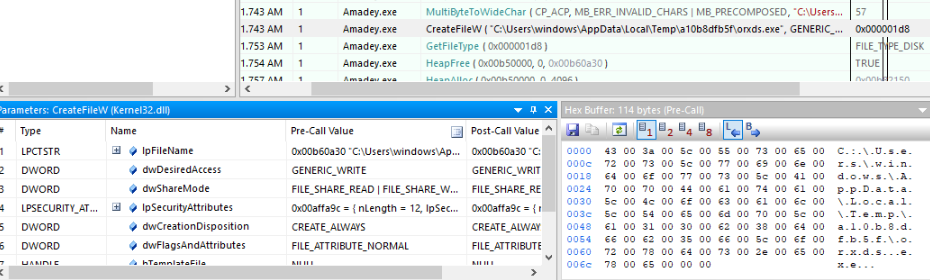
API Monitor is exactly as its name describes, it’s used to monitor every Windows API that the sample has called, using this tool can get us insights into how the sample utilizes Windows APIs and it also provides us with these API calls stored alongside with each parameter passed to each one, which enables us to extract extremely useful information from there.
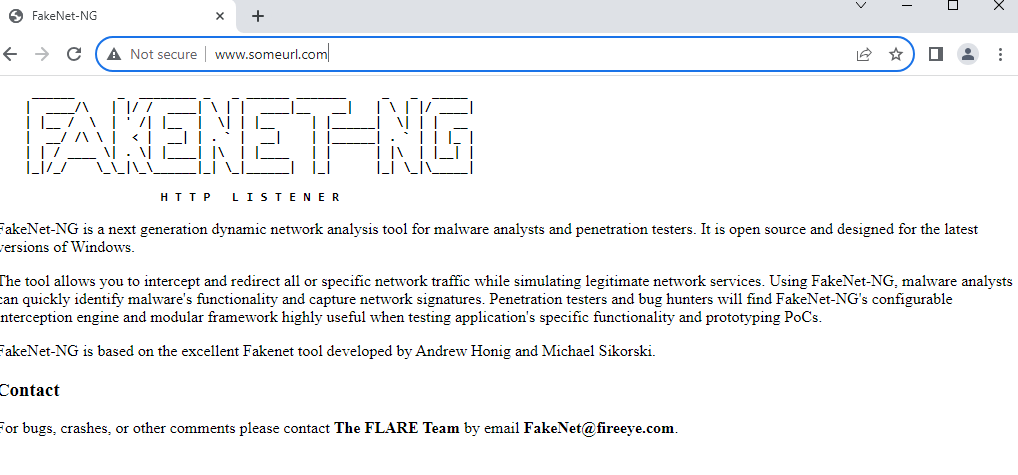
Typically in a malware analysis environment, we disconnect it from the internet to prevent it from communicating with the world out there, but sometimes the malware doesn’t reveal its functionality if it can’t reach out to the internet, FAKENET-NG is a great tool to fake that network communication as it will listen to any connection requested and respond back with a dummy respond and some times that works and tricks the malware to continue execution.
Also, it stores the entire traffic in a pcap file we can investigate it later.
Here we can see some dummy data returned when visiting a randomly named URL.
IDA has a great script engine that can really serve you well if you manage to use it and write your own scripts, but as this is not the topic of this blog post let’s take a look at some existing IDA scripts “Plugins” that can make your life easier.
Capa is a really great plugin to run at first after loading your sample into IDA, it has great power you can benefit from as it runs a large number of rules against the sample to identify capabilities and get you all the found functionalities with the addresses of the functions that implement these functionalities.
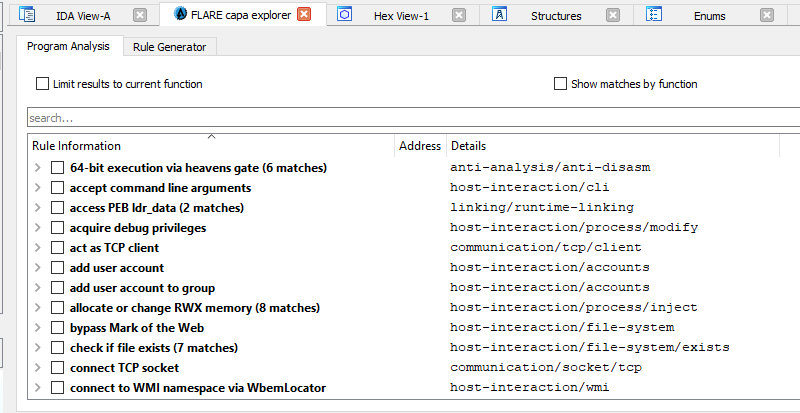
AutoRE is also a good plugin to run at the start of your analysis as it shows you a mapping of which APIs are called from each function and it categorizes them for you, this can make you able to rename function to more clear names before starting your analysis.
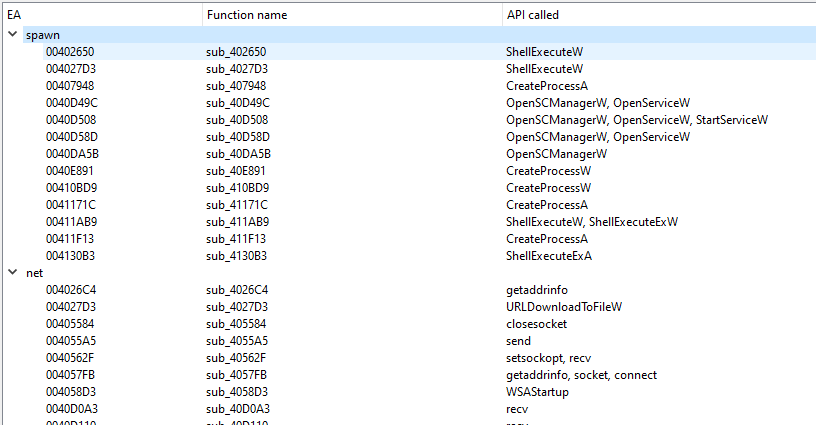
Emulation tools are a great addition to have in your arsenal, these tools are capable of saving you a lot of time reversing an encryption function or repeating a specific task, as emulation gives you the ability to script the execution of your sample.
qiling is a great framework for emulation that supports various architectures and OSs.
Let’s take a simple example and see how this works.
here we can see an encrypted stack string gets decrypted, so we can use emulation to execute this part of the code from any start address we want, let it execute until it decrypts itself, and then we can print the decrypted value.
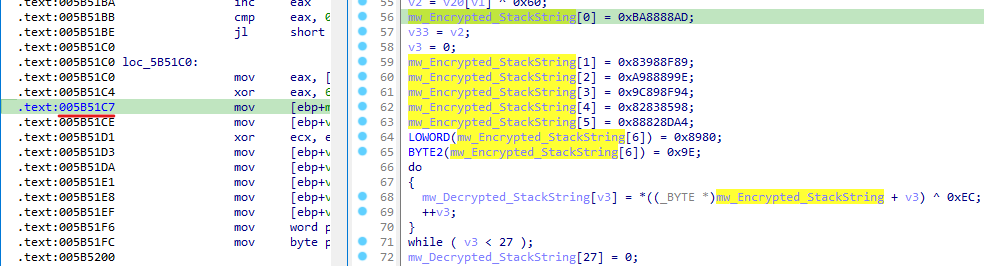
and here we can see the decrypted value address is stored in “EDX”, so we can set the end point after that instruction.
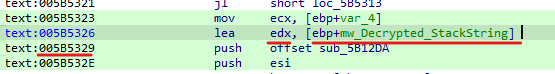
here is the example string to do that.
from qiling import *
ql = Qiling(["../../examples/rootfs/x86_windows/bin/pika.bin"], "../../examples/rootfs/x86_windows")
esp = ql.arch.regs.read("ESP")
ql.arch.regs.write("EBP", esp)
ql.run(begin = 0x005B51C7, end = 0x005B5329)
edx = ql.arch.regs.read("EDX")
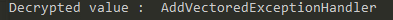
print("Decrypted value : ",ql.mem.string(edx))when we run the script, we can get the decrypted value.
setting up a good analysis machine and using useful tools can make our analysis much easier and more effective, this is not a comprehensive list of tools, these are just the tools that present in my arsenal, a lot of other great tools maybe not be mentioned here as the number of tools is huge out there and depends on the analyst and his needs, if you have an interesting tool to share or add it here, don’t hesitate to reach out to me here.
Author:Amr Ashraf